Raccoon Stealer malware returns with new stealthier version
The developers of Raccoon Stealer information-stealing malware have ended their 6-month hiatus from hacker forums to promote a new 2.3.0 version of the malware to cyber criminals.
Raccoon is one of the most well-known and widely used information-stealing malware families, having been around since 2019, sold via a subscription model for $200/month to threat actors.
The malware steals data from over 60 applications, including login credentials, credit card information, browsing history, cookies, and cryptocurrency wallet accounts.
The project entered a period of uncertainty in October 2022, when its primary author, Mark Sokolovsky, was arrested in the Netherlands, and the FBI took down the then malware-as-a-service's infrastructure.
The Raccoon is back
In a new post to a hacker forum first spotted by VX-Underground, the malware's current authors informed the cybercriminal community that they're back, having spent their time "working tirelessly" to bring them new features that will enrich the user experience.
These new features were implemented after "customer" feedback, requests, and cybercrime trends, aiming to keep the malware in the top tier of the info-stealers market.
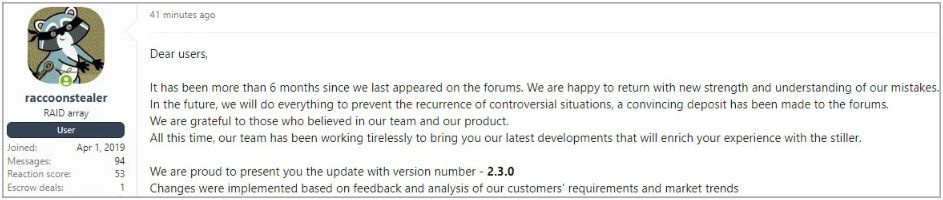
Announcement of Raccoon v2.3.0 on hacker forums
Source: @vxunderground
A report by Cyberint says that Raccoon 2.3.0 has introduced several "quality of life" and OpSec improvements that make it easier and safer to use, making it easier to use for less skilled threat actors and less likely for them to be traced by researchers and law enforcement.
First, a new quick search tool in the Raccoon Stealer dashboard allows hackers to easily find specific stolen data and retrieve credentials, documents, or other stolen data from massive datasets.
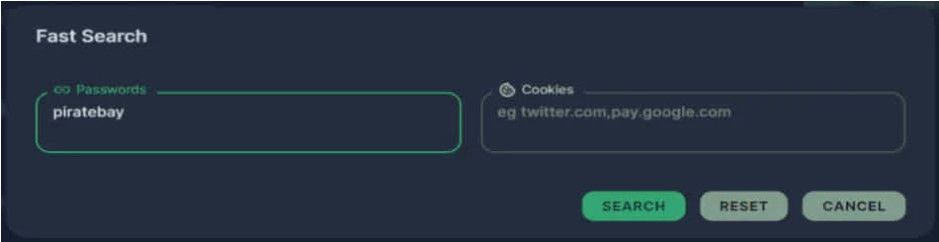
Raccoon's new search tool
Source: Cyberint
Secondly, the new Raccoon version features a system that counters suspicious activities that might be related to security-assisting bots, like multiple access events generated from the same IP.
In those cases, Raccoon will automatically delete the corresponding records and update all client pads accordingly.
The user can now see the activity profile score of each IP address right from the malware's dashboard, where green, yellow, and red smiley icons indicate the probability of bot activity.
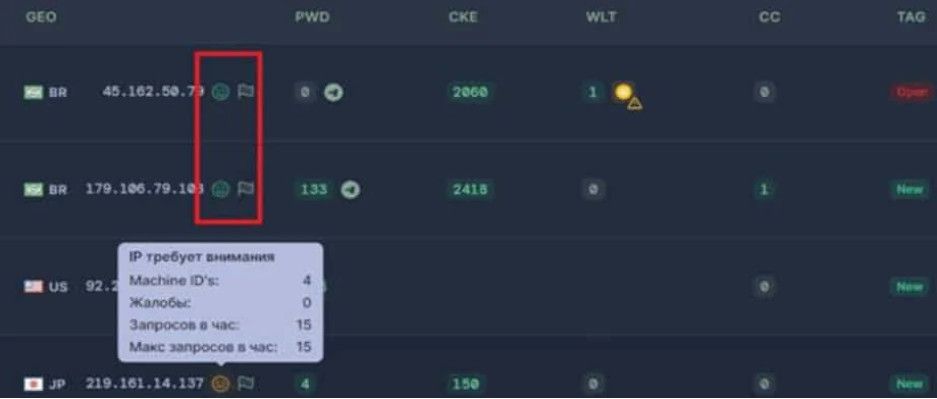
Smileys used for indicating likelihood of bot activity
Source: Cyberint
A third important new feature incorporated as a protective measure against security researchers is a reporting system that detects and blocks IPs used by crawlers and bots that cyber-intelligence firms use to monitor Raccoon's traffic.
Finally, a new Log Stats panel gives users a "quick-glance" overview of their operations, the most successfully targeted regions, the number of breached computers, etc.
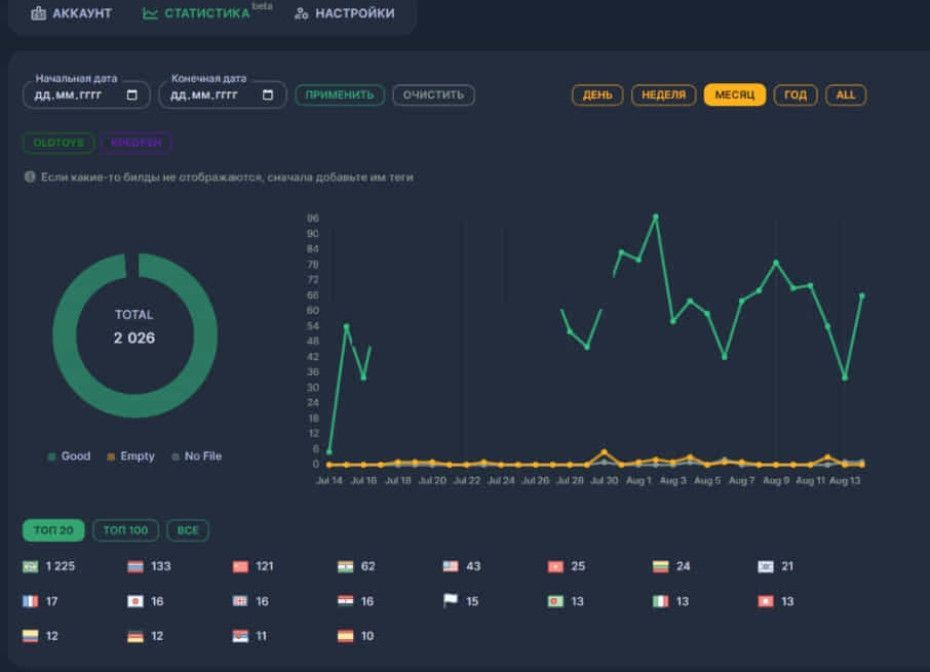
New log graphs screen
Source: Cyberint
Information stealers constitute a massive threat to both home users and businesses, as their widespread adoption by the cybercrime community ensures payloads are through a myriad of channels, reaching a a large and diverse audience.
As this type of malware not only steals credentials, but also cookies, it could allow threat actors to use those stolen session cookies to bypass multi-factor authentication and breach corporate networks. Once they establish a foothold on the network, it could lead to a variety of attacks, including data theft, ransomware, BEC scams, and cyber espionage.
To protect against Raccoon Stealer and all infostealers, password managers should be used instead of storing credentials on the browser.
Furthermore, multi-factor authentication should be enabled on all accounts and avoid downloading executables from dubious websites even if redirected there from legitimate sources such as Google Ads, YouTube videos, or Facebook posts.
Source: bleepingcomputer.com
Bạn cũng có thể quan tâm
All Rights Reserved | John&Partners LLC.






