Lazarus hackers hijack Microsoft IIS servers to spread malware
The North Korean state-sponsored Lazarus hacking group is breaching Windows Internet Information Service (IIS) web servers to hijack them for malware distribution.
IIS is Microsoft's web server solution used to host websites or application services, such as Microsoft Exchange's Outlook on the Web.
South Korean security analysts at ASEC previously reported that Lazarus was targeting IIS servers for initial access to corporate networks. On July 24, the cybersecurity company says that the threat group leverages poorly protected IIS services for malware distribution too.
The main advantage of this technique is the ease of infecting visitors of websites or users of services hosted on breached IIS servers owned by trustworthy organizations.
Attacks on South Korea
In the recent attacks observed by ASEC's analysts, Lazarus compromised legitimate South Korean websites to perform 'Watering Hole' attacks on visitors using a vulnerable version of the INISAFE CrossWeb EX V6 software.
Many public and private organizations in South Korea use this particular software for electronic financial transactions, security certification, internet banking, etc.
The INISAFE vulnerability was previously documented by both Symantec and ASEC in 2022, explaining that it was exploited using HTML email attachments at the time.
"A typical attack begins when a malicious HTM file is received, likely as a malicious link in an email or downloaded from the web. The HTM file is copied to a DLL file called scskapplink.dll and injected into the legitimate system management software INISAFE Web EX Client," explains the 2022 report by Symantec.
Exploiting the flaw fetches a malicious 'SCSKAppLink.dll' payload from an IIS web server already compromised before the attack for use as a malware distribution server.
"The download URL for 'SCSKAppLink.dll' was identified as being the aforementioned IIS web server," explains ASEC's new report.
"This signifies that the threat actor attacked and gained control over IIS web servers before using these as servers for distributing malware."
ASEC did not analyze the particular payload but says it is likely a malware downloader seen in other recent Lazarus campaigns.
Next, Lazarus uses the 'JuicyPotato' privilege escalation malware ('usopriv.exe') to gain higher-level access to the compromised system.
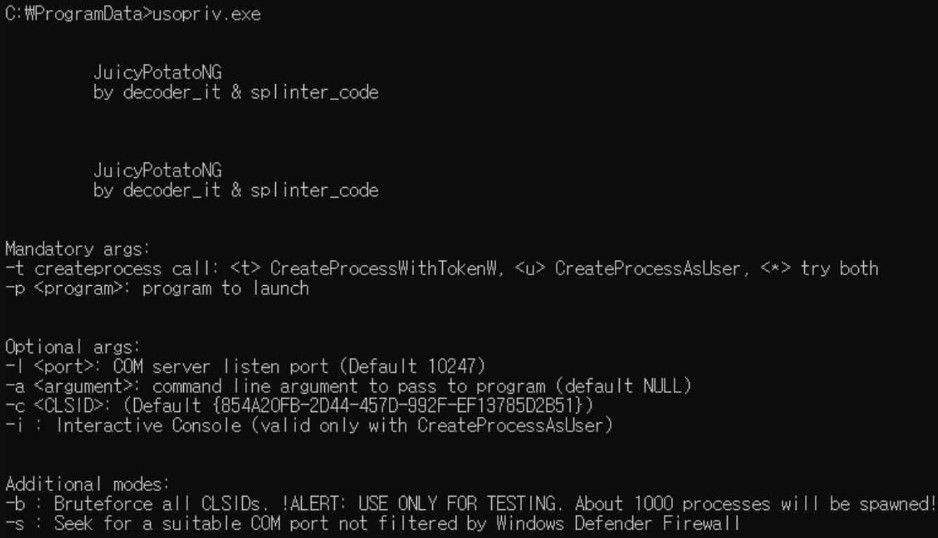
JuicyPotato in action (ASEC)
JuicyPotato is used for executing a second malware loader ('usoshared.dat') that decrypts downloaded data files and executes them into memory for AV evasion.
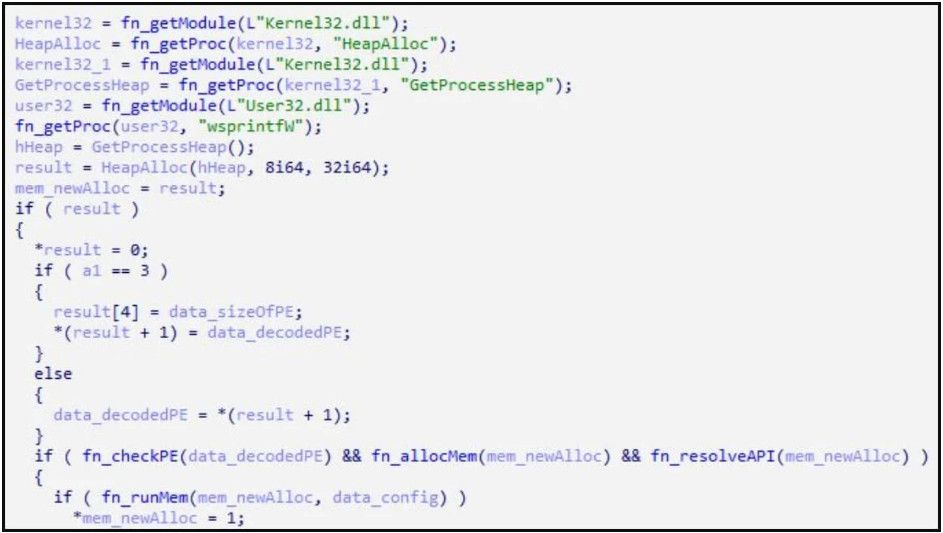
Loading the decrypted executable in memory (ASEC)
ASEC recommends that NISAFE CrossWeb EX V6 users update the software to its latest version, as Lazarus' exploitation of known vulnerabilities in the product has been underway since at least April 2022.
The security company advises users to upgrade to version 3.3.2.41 or later and points to remediation instructions it posted four months ago, highlighting the Lazarus threat.
Microsoft application servers are becoming a popular target for hackers to use in malware distribution, likely due to their trusted nature.
Just last week, CERT-UA and Microsoft reported that Russian Turla hackers were using compromised Microsoft Exchange servers to deliver backdoors to their targets.
Source: bleepingcomputer.com
Bạn cũng có thể quan tâm
All Rights Reserved | John&Partners LLC.






