EvilProxy phishing campaign targets 120,000 Microsoft 365 users
EvilProxy is becoming one of the more popular phishing platforms to target MFA-protected accounts, with researchers seeing 120,000 phishing emails sent to over a hundred organizations to steal Microsoft 365 accounts.
This new research comes from Proofpoint, which warns of a dramatic surge of successful cloud account takeover incidents in the past five months, impacting primarily high-ranking executives.
The cybersecurity company has observed a very large-scale campaign supported by EvilProxy, which combines brand impersonation, bot detection evasion, and open redirections.
EvilProxy attacks
EvilProxy is a phishing-as-a-service platform that employs reverse proxies to relay authentication requests and user credentials between the user (target) and the legitimate service website.
As the phishing server proxies the legitimate login form, it can steal authentication cookies once a user logs into their account.
Furthermore, as the user already had to pass MFA challenges when logging into an account, the stolen cookie allows the threat actors to bypass multi-factor authentication.
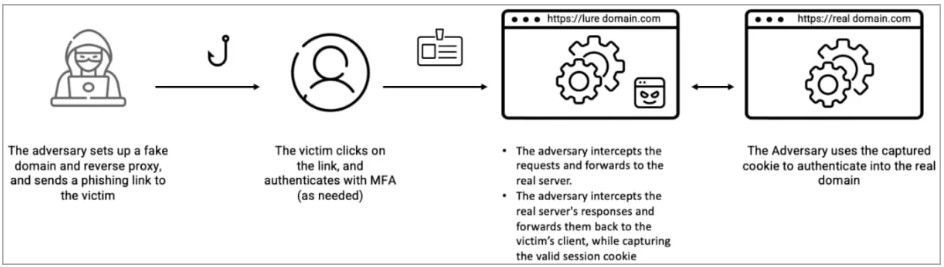
EvilProxy phishing attack flow
Source: Proofpoint
As reported in September 2022 by Resecurity, EvilProxy is sold to cyber criminals for $400/month, promising the ability to target Apple, Google, Facebook, Microsoft, Twitter, GitHub, GoDaddy, and PyPI accounts.
A new phishing campaign observed by Proofpoint since March 2023 is using the EvilProxy service to send emails that impersonate popular brands like Adobe, DocuSign, and Concur.
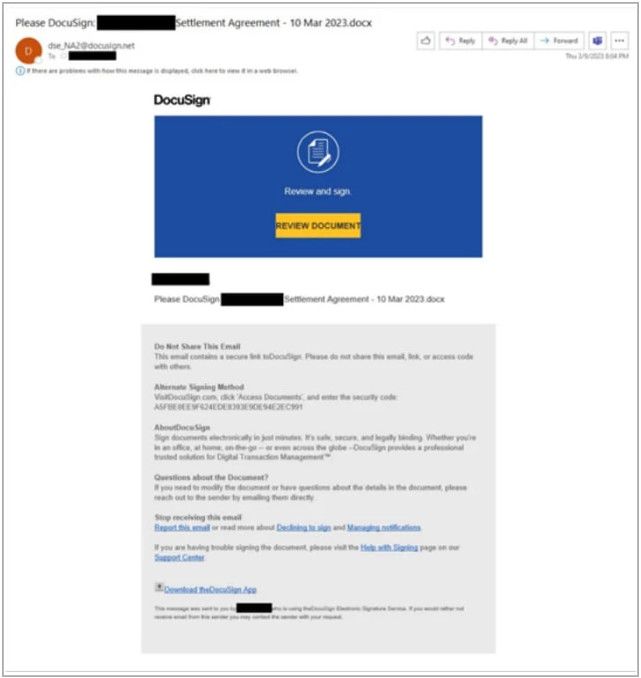
Phishing email used in this campaign
Source: Proofpoint
If the victim clicks on the embedded link, they go through an open redirection via YouTube or SlickDeals, followed by a series of subsequent redirections that aim to lower the chances of discovery and analysis.
Eventually, the victim lands on an EvilProxy phishing page that reverse proxies the Microsoft 365 login page, which also features the victim's organization theme to appear authentic.
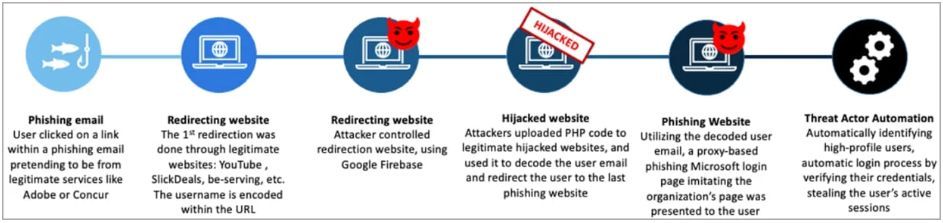
Attack stages
Source: Proofpoint
"In order to hide the user email from automatic scanning tools, the attackers employed special encoding of the user email, and used legitimate websites that have been hacked, to upload their PHP code to decode the email address of a particular user," explains Proofpoint.
"After decoding the email address, the user was forwarded to the final website – the actual phishing page, tailor-made just for that target’s organization."
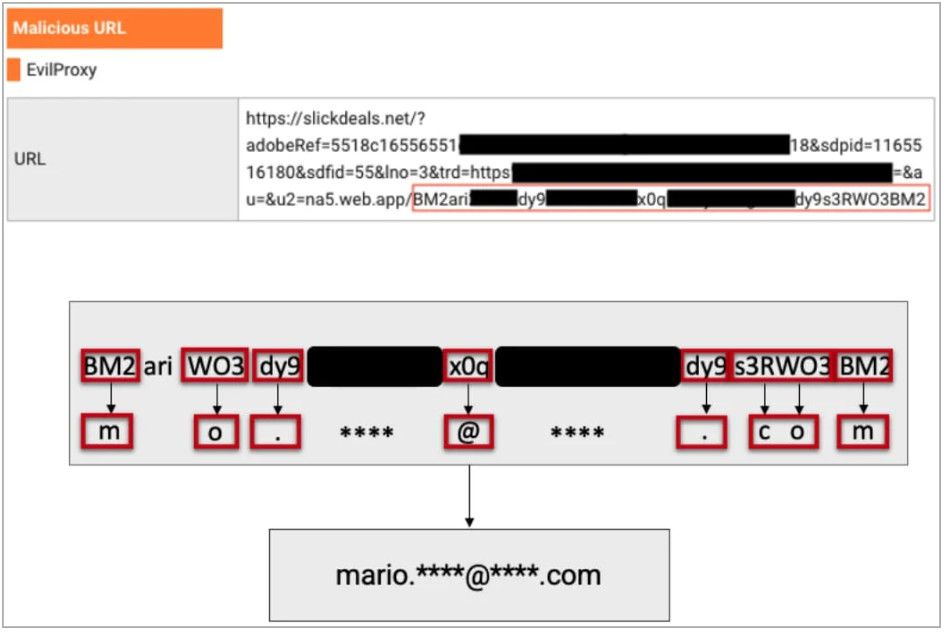
Decoding the target's email address
Source: Proofpoint
Targeting peculiarities
The researchers discovered that the latest campaign redirects users with a Turkish IP address to a legitimate site instead, essentially calling off the attack, which might mean that the operation is based in Turkey.
Also, Proofpoint noticed that the attackers were very selective with which cases they would proceed to the account takeover phase, prioritizing "VIP" targets and ignoring those lower in the hierarchy.
Of those whose accounts were breached, 39% were C-level executives, 9% were CEOs and vice presidents, 17% were chief financial officers, and the rest were employees with access to financial assets or sensitive information.
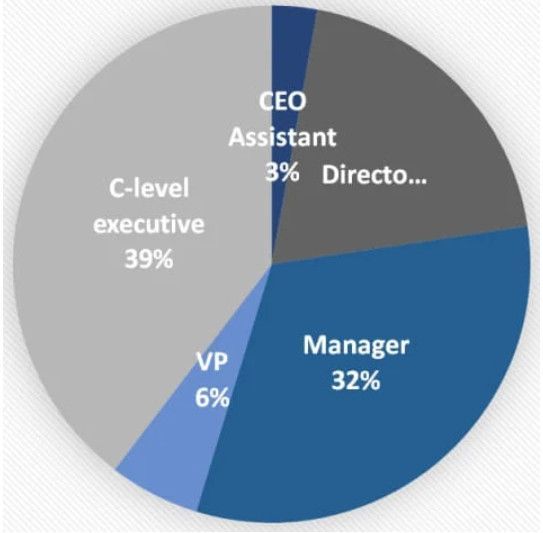
Compromised targets
Source: Proofpoint
Once a Microsoft 365 account is compromised, the threat actors add their own multi-factor authentication method (via Authenticator App with Notification and Code) to establish persistence.
Reverse proxy phishing kits, and EvilProxy in particular, are a growing threat capable of delivering high-quality phishing at dangerous scales while bypassing security measures and account protections.
Organizations can only defend against this threat through higher security awareness, stricter email filtering rules, and adopting FIDO-based physical keys.
Source: bleepingcomputer.com
Bạn cũng có thể quan tâm
All Rights Reserved | John&Partners LLC.






