CISA warns govt agencies to secure iPhones against spyware attacks
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) ordered federal agencies on September 11th to patch security vulnerabilities abused as part of a zero-click iMessage exploit chain to infect iPhones with NSO Group's Pegasus spyware.
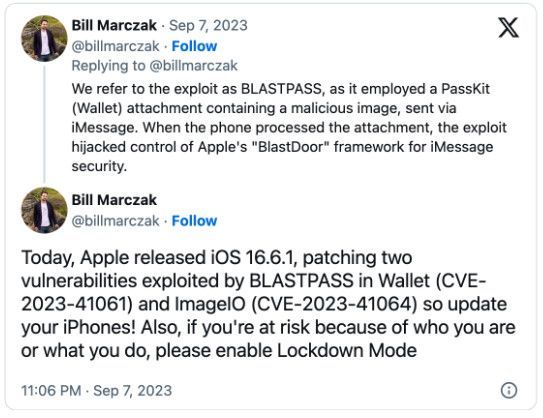
This warning comes after Citizen Lab disclosed that the two flaws were used to compromise fully-patched iPhones belonging to a Washington DC-based civil society organization using an exploit chain named BLASTPASS that worked via PassKit attachments containing malicious images.
Citizen Lab also warned Apple customers to apply emergency updates issued on Thursday, September 7th immediately and urged individuals susceptible to targeted attacks due to their identity or occupation to enable Lockdown Mode.
"Apple is aware of a report that this issue may have been actively exploited," the company said when describing the two Image I/O and Wallet vulnerabilities, tracked as CVE-2023-41064 and CVE-2023-41061.
The list of impacted devices is quite extensive, as the bugs affect both older and newer models, and it includes:
- iPhone 8 and later
- iPad Pro (all models), iPad Air 3rd generation and later, iPad 5th generation and later, and iPad mini 5th generation and later
- Macs running macOS Ventura
- Apple Watch Series 4 and later
Apple fixed the two zero-days in macOS Ventura 13.5.2, iOS 16.6.1, iPadOS 16.6.1, and watchOS 9.6.2 with memory handling and improved logic. Both allow attackers to gain arbitrary code execution on unpatched devices.
October 2nd patch deadline
On Monday, September 4th, CISA added the two security flaws to its Known Exploited Vulnerabilities catalog, tagging them as "frequent attack vectors for malicious cyber actors" and posing "significant risks to the federal enterprise."
U.S. Federal Civilian Executive Branch Agencies (FCEB) must patch all vulnerabilities added to CISA's KEV catalog within a limited timeframe, per a binding operational directive (BOD 22-01) published in November 2022.
After September 11th's update, federal agencies must secure all vulnerable iOS, iPadOS, and macOS devices on their networks against CVE-2023-41064 and CVE-2023-41061 by October 2nd, 2023.
While BOD 22-01 primarily focuses on U.S. federal agencies, CISA also strongly advised private companies to prioritize patching the two vulnerabilities as soon as possible.
Since January 2023, Apple fixed a total of 13 zero-days exploited to target iOS, macOS, iPadOS, and watchOS devices, including:
- two zero-days (CVE-2023-37450 and CVE-2023-38606) in July
- three zero-days (CVE-2023-32434, CVE-2023-32435, and CVE-2023-32439) in June
- three more zero-days (CVE-2023-32409, CVE-2023-28204, and CVE-2023-32373) in May
- two zero-days (CVE-2023-28206 and CVE-2023-28205) in April
- and a WebKit zero-day (CVE-2023-23529) in February
Source: bleepingcomputer.com
Bạn cũng có thể quan tâm
All Rights Reserved | John&Partners LLC.






