Atomic Stealer malware strikes macOS via fake browser updates
The 'ClearFake' fake browser update campaign has expanded to macOS, targeting Apple computers with Atomic Stealer (AMOS) malware.
The ClearFake campaign started in July this year to target Windows users with fake Chrome update prompts that appear on breached sites via JavaScript injections.
In October 2023, Guardio Labs discovered a significant development for the malicious operation, which leveraged Binance Smart Chain contracts to hide its malicious scripts supporting the infection chain in the blockchain.
Via this technique, dubbed "EtherHiding," the operators distributed Windows-targeting payloads, including information-stealing malware like RedLine, Amadey, and Lumma.
Expanding to macOS
On November 17, 2023, threat analyst Ankit Anubhav reported that ClearFake had started pushing DMG payloads to macOS users visiting compromised websites.
A Malwarebytes report from earlier last week confirms this development, reporting that these attacks employ a Safari update bait along with the standard Chrome overlay.
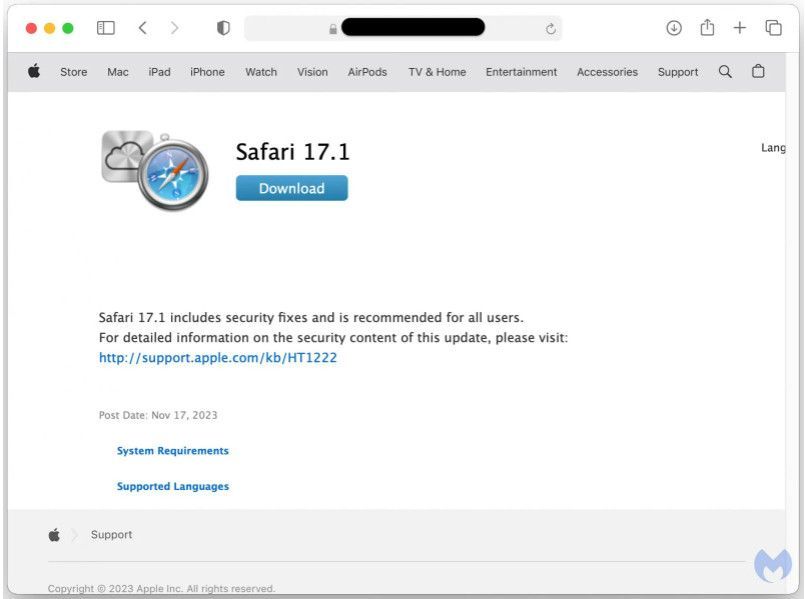
Fake update overlay targeting macOS users
Source: Malwarebytes
The payload dropped in these cases is Atomic, an info-stealing malware sold to cybercriminals via Telegram channels for $1,000/month.

Atomic stealer disguised as a Safari update
Source: Malwarebytes
Atomic was discovered in April 2023 by Trellix and Cyble, who reported that it attempts to steal passwords, cookies, and credit cards stored in browsers, local files, data from over 50 cryptocurrency extensions, and keychain passwords.
The keychain password is macOS' built-in password manager that holds WiFi passwords, website logins, credit card data, and other encrypted information, so its compromise can result in a significant breach for the victim.
Malwarebyte's examination of the payload's strings reveals a series of commands for extracting sensitive data like passwords and targeting document files, images, crypto wallet files, and keys.
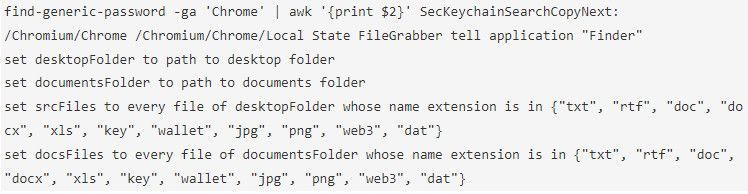
String of commands in Atomic's code
Source: Malwarebytes
The ClearFake campaign now targeting Macs is a reminder for Apple users to strengthen their security and be careful with downloads, especially prompts to update your browser when visiting websites.
Even after several months following the discovery and reports on Atomic, the payload is undetected by roughly 50% of AV engines on VirusTotal.
Furthermore, all Safari browser updates will be distributed through macOS's Software Update, or for other browsers, within the browser itself.
Therefore, if you see any prompts to download browser updates on websites, they should be ignored.
Source: bleepingcomputer.com
Bạn cũng có thể quan tâm
All Rights Reserved | John&Partners LLC.






