Apple fixes new zero-day used in attacks against iPhones, Macs
Apple has released security updates to address zero-day vulnerabilities exploited in attacks targeting iPhones, Macs, and iPads.
"Apple is aware of a report that this issue may have been actively exploited," the company said in an advisory describing a WebKit flaw tracked as CVE-2023-37450 that was addressed in a new round of Rapid Security Response (RSR) updates earlier July.
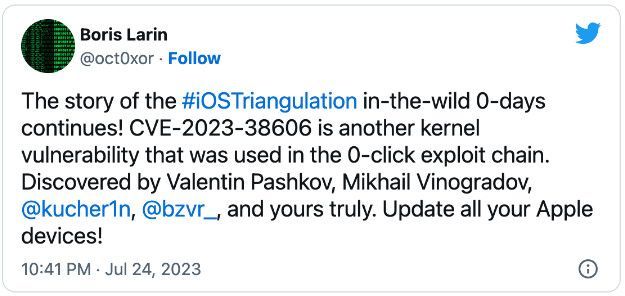
The other zero-day patched on July 24 is a new Kernel flaw tracked as CVE-2023-38606 that was exploited in attacks targeting devices running older iOS releases.
"Apple is aware of a report that this issue may have been actively exploited against versions of iOS released before iOS 15.7.1," the company said.
Attackers could exploit it on unpatched devices to modify sensitive kernel states. Apple addressed the two weaknesses with improved checks and state management.
CVE-2023-38606 is part of a zero-click exploit chain used to deploy Triangulation spyware on iPhones via iMessage exploits, according to Kaspersky GReAT lead security researcher Boris Larin.
The company also backported security patches for a zero-day (CVE-2023-32409) addressed in May to devices running tvOS 16.6 and watchOS 9.6.
Apple addressed the three zero-days in macOS Ventura 13.5, iOS and iPadOS 16.6, tvOS 16.6, watchOS 9.6, and Safari 16.6 with improved bounds checks, input validation, and memory management.
The list of devices impacted by the zero-days fixed on July 24 is quite extensive, and it includes a wide range of iPhone and iPad models, as well as Macs running macOS Big Sur, Monterey, and Ventura.
Eleventh zero-day exploited in attacks patched this year
Since the start of the year, Apple has patched 11 zero-day flaws exploited by attackers to target devices running iOS, macOS, and iPadOS.
Earlier July, Apple released out-of-band Rapid Security Response (RSR) updates to address a bug (CVE-2023-37450) impacting fully-patched iPhones, Macs, and iPads.
The company later confirmed the RSR updates broke web browsing on some websites and released fixed versions of the buggy patches two days later.
Before this, Apple also addressed:
- three zero-days (CVE-2023-32434, CVE-2023-32435, and CVE-2023-32439) in June
- three more zero-days (CVE-2023-32409, CVE-2023-28204, and CVE-2023-32373) in May
- two zero-days (CVE-2023-28206 and CVE-2023-28205) in April
- and another WebKit zero-day (CVE-2023-23529) in February
Source: bleepingcomputer.com
Bạn cũng có thể quan tâm
All Rights Reserved | John&Partners LLC.






