What is cybersecurity?
Cybersecurity is the protection of internet-connected systems such as hardware, software and data from cyberthreats. The practice is used by individuals and enterprises to protect against unauthorized access to data centers and other computerized systems.
A strong cybersecurity strategy can provide a good security posture against malicious attacks designed to access, alter, delete, destroy or extort an organization's or user's systems and sensitive data. Cybersecurity is also instrumental in preventing attacks that aim to disable or disrupt a system's or device's operations.
Why is cybersecurity important?
With an increasing number of users, devices and programs in the modern enterprise, combined with the increased deluge of data -- much of which is sensitive or confidential -- the importance of cybersecurity continues to grow. The growing volume and sophistication of cyber attackers and attack techniques compound the problem even further.
What are the elements of cybersecurity and how does it work?
The cybersecurity field can be broken down into several different sections, the coordination of which within the organization is crucial to the success of a cybersecurity program. These sections include the following:
- Application security
- Information or data security
- Network security
- Disaster recovery/business continuity planning
- Operational security
- Cloud security
- Critical infrastructure security
- Physical security
- End-user education
Maintaining cybersecurity in a constantly evolving threat landscape is a challenge for all organizations. Traditional reactive approaches, in which resources were put toward protecting systems against the biggest known threats, while lesser known threats were undefended, is no longer a sufficient tactic. To keep up with changing security risks, a more proactive and adaptive approach is necessary. Several key cybersecurity advisory organizations offer guidance. For example, the National Institute of Standards and Technology (NIST) recommends adopting continuous monitoring and real-time assessments as part of a risk assessment framework to defend against known and unknown threats.
What are the benefits of cybersecurity?
The benefits of implementing and maintaining cybersecurity practices include:
- Business protection against cyberattacks and data breaches.
- Protection for data and networks.
- Prevention of unauthorized user access.
- Improved recovery time after a breach.
- Protection for end users and endpoint devices.
- Regulatory compliance.
- Business continuity.
- Improved confidence in the company's reputation and trust for developers, partners, customers, stakeholders and employees.
What are the different types of cybersecurity threats?
The process of keeping up with new technologies, security trends and threat intelligence is a challenging task. It is necessary in order to protect information and other assets from cyberthreats, which take many forms. Types of cyberthreats include:
- Malware is a form of malicious software in which any file or program can be used to harm a computer user. This includes worms, viruses, Trojans and spyware.
- Ransomware is another type of malware. It involves an attacker locking the victim's computer system files -- typically through encryption -- and demanding a payment to decrypt and unlock them.
- Social engineering is an attack that relies on human interaction to trick users into breaking security procedures to gain sensitive information that is typically protected.
- Phishing is a form of social engineering where fraudulent email or text messages that resemble those from reputable or known sources are sent. Often random attacks, the intent of these messages is to steal sensitive data, such as credit card or login information.
- Spear phishing is a type of phishing attack that has an intended target user, organization or business.
- Insider threats are security breaches or losses caused by humans -- for example, employees, contractors or customers. Insider threats can be malicious or negligent in nature.
- Distributed denial-of-service (DDoS) attacks are those in which multiple systems disrupt the traffic of a targeted system, such as a server, website or other network resource. By flooding the target with messages, connection requests or packets, the attackers can slow the system or crash it, preventing legitimate traffic from using it.
- Advanced persistent threats (APTs) are prolonged targeted attacks in which an attacker infiltrates a network and remains undetected for long periods of time with the aim to steal data.
- Man-in-the-middle (MitM) attacks are eavesdropping attacks that involve an attacker intercepting and relaying messages between two parties who believe they are communicating with each other.
Other common attacks include botnets, drive-by-download attacks, exploit kits, malvertising, vishing, credential stuffing attacks, cross-site scripting (XSS) attacks, SQL injection attacks, business email compromise (BEC) and zero-day exploits.
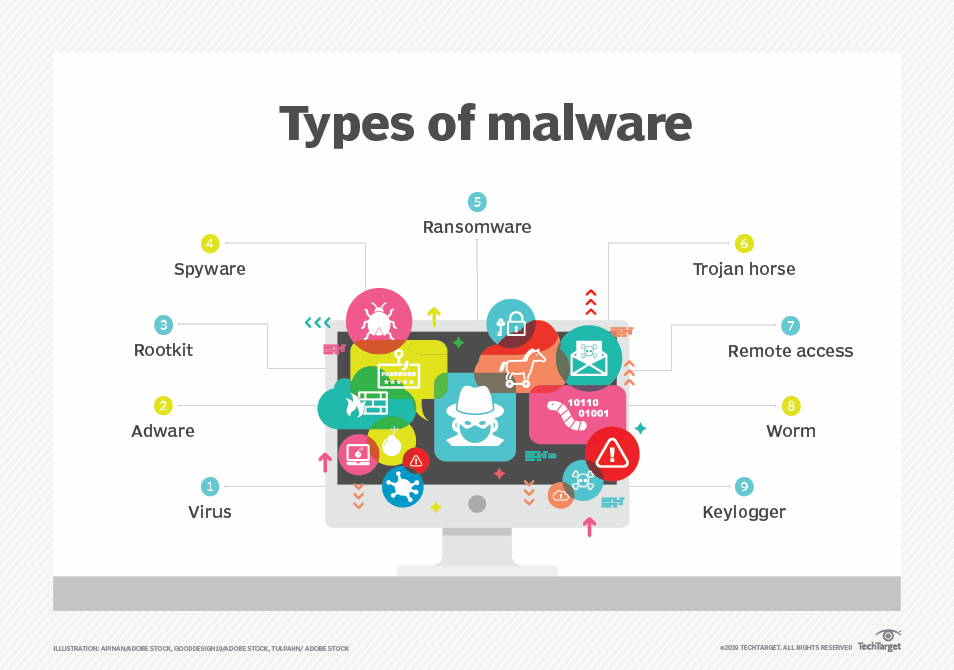
Malware variants vary, from ransomware to worm to virus
What are the top cybersecurity challenges?
Cybersecurity is continually challenged by hackers, data loss, privacy, risk management and changing cybersecurity strategies. The number of cyberattacks is not expected to decrease in the near future. Moreover, increased entry points for attacks, such as with the arrival of the internet of things (IoT), increase the need to secure networks and devices.
One of the most problematic elements of cybersecurity is the evolving nature of security risks. As new technologies emerge, and as technology is used in new or different ways, new attack avenues are developed. Keeping up with these frequent changes and advances in attacks, as well as updating practices to protect against them, can be challenging. Issues include ensuring all elements of cybersecurity are continually updated to protect against potential vulnerabilities. This can be especially difficult for smaller organizations without the staff or in-house resources.
Additionally, organizations can gather a lot of potential data on individuals who use one or more of their services. With more data being collected, the likelihood of a cybercriminal who wants to steal personally identifiable information (PII) is another concern. For example, an organization that stores PII in the cloud may be subject to a ransomware attack. Organizations should do what they can to prevent a cloud breach.
Cybersecurity programs should also address end-user education, as employees may accidently bring viruses into the workplace on their laptops or mobile devices. Regular security awareness training will help employees do their part in keeping their company safe from cyberthreats.
Another challenge to cybersecurity includes a shortage of qualified cybersecurity personnel. As the amount of data collected and used by businesses grows, the need for cybersecurity staff to analyze, manage and respond to incidents also increases. (ISC)2 estimated the workplace gap between needed cybersecurity jobs and security professionals at 3.1 million.
How is automation used in cybersecurity?
Automation has become an integral component to keep companies protected from the growing number and sophistication of cyberthreats. Using artificial intelligence (AI) and machine learning in areas with high-volume data streams can help improve cybersecurity in three main categories:
- Threat detection. AI platforms can analyze data and recognize known threats, as well as predict novel threats.
- Threat response. AI platforms also create and automatically enact security protections.
- Human augmentation. Security pros are often overloaded with alerts and repetitive tasks. AI can help eliminate alert fatigue by automatically triaging low-risk alarms and automating big data analysis and other repetitive tasks, freeing humans for more sophisticated tasks.
Other benefits of automation in cybersecurity include attack classification, malware classification, traffic analysis, compliance analysis and more.
Cybersecurity vendors and tools
Vendors in the cybersecurity field typically offer a variety of security products and services. Common security tools and systems include:
- Identity and access management (IAM)
- Firewalls
- Endpoint protection
- Antimalware
- Intrusion prevention/detection systems (IPS/IDS)
- Data loss prevention (DLP)
- Endpoint detection and response
- Security information and event management (SIEM)
- Encryption tools
- Vulnerability scanners
- Virtual private networks (VPNs)
- Cloud workload protection platform (CWPP)
- Cloud access security broker (CASB)
Well-known cybersecurity vendors include Check Point, Cisco, Code42, CrowdStrike, FireEye, Fortinet, IBM, Imperva, KnowBe4, McAfee, Microsoft, Palo Alto Networks, Rapid7, Splunk, Symantec, Trend Micro and Trustwave.
What are the career opportunities in cybersecurity?
As the cyberthreat landscape continues to grow and new threats emerge -- such as IoT threats -- individuals are needed with cybersecurity awareness and hardware and software skills.
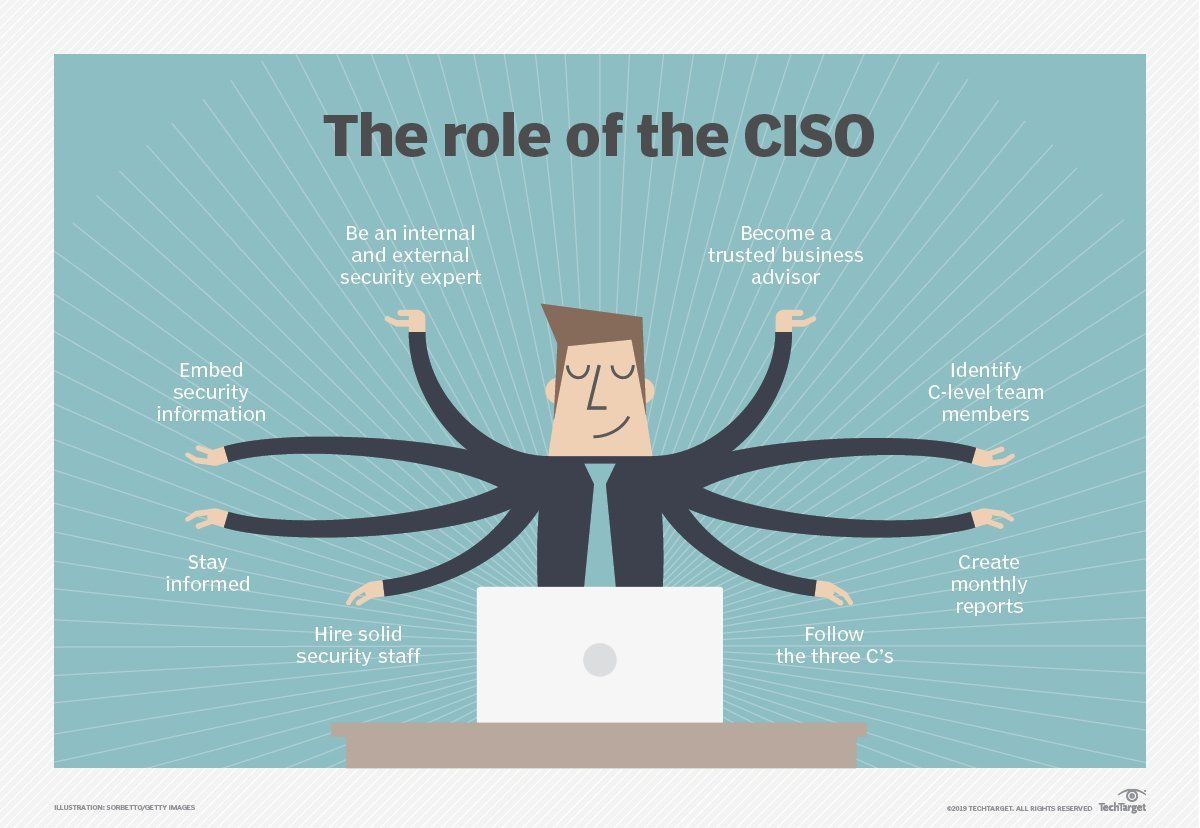
CISO tasks range widely to maintain enterprise cybersecurity
IT professionals and other computer specialists are needed in security roles, such as:
- Chief information security officer (CISO) is the individual who implements the security program across the organization and oversees the IT security department's operations.
- Chief security office (CSO) is the executive responsible for the physical and/or cybersecurity of a company.
- Security engineers protect company assets from threats with a focus on quality control within the IT infrastructure.
- Security architects are responsible for planning, analyzing, designing, testing, maintaining and supporting an enterprise's critical infrastructure.
- Security analysts have several responsibilities that include planning security measures and controls, protecting digital files, and conducting both internal and external security audits.
- Penetration testers are ethical hackers who test the security of systems, networks and applications, seeking vulnerabilities that could be exploited by malicious actors.
- Threat hunters are threat analysts who aim to uncover vulnerabilities and attacks and mitigate them before they compromise a business.
Other cybersecurity careers include security consultants, data protection officer, cloud security architects, security operations manager (SOC) managers and analysts, security investigators, cryptographers and security administrators.
Source: techtarget.com
Bạn cũng có thể quan tâm
All Rights Reserved | John&Partners LLC.






