TP-Link smart bulbs can let hackers steal your WiFi password
Researchers from Italy and the UK have discovered four vulnerabilities in the TP-Link Tapo L530E smart bulb and TP-Link’s Tapo app, which could allow attackers to steal their target’s WiFi password.
TP-Link Tapo L530E is a top-selling smart bulb on multiple marketplaces, including Amazon. TP-link Tapo is a smart device management app with 10 million installations on Google Play.

The Tapo L530E (TP-Link)
The researchers from Universita di Catania and the University of London analyzed this product due to its popularity. However, the goal of their paper is to underscore security risks in the billions of smart IoT devices used by consumers, many of which follow risky data transmission and lackluster authentication safeguards.
Smart bulb flaws
The first vulnerability concerns improper authentication on Tapo L503E, allowing attackers to impersonate the device during the session key exchange step.
This high-severity vulnerability (CVSS v3.1 score: 8.8) allows an adjacent attacker to retrieve Tapo user passwords and manipulate Tapo devices.
The second flaw is also a high-severity issue (CVSS v3.1 score: 7.6) arising from a hard-coded short checksum shared secret, which attackers can obtain through brute-forcing or by decompiling the Tapo app.
The third problem is a medium-severity flaw concerning the lack of randomness during symmetric encryption that makes the cryptographic scheme predictable.
Finally, a fourth issue stems from the lack of checks for the freshness of received messages, keeping session keys valid for 24 hours, and allowing attackers to replay messages during that period.
Attack scenarios
The most worrying attack scenario is bulb impersonation and retrieval of Tapo user account details by exploiting vulnerabilities 1 and 2.
Then, by accessing the Tapo app, the attacker can extract the victim’s WiFi SSID and password and gain access to all other devices connected to that network.
The device needs to be in setup mode for the attack to work. However, the attacker can deauthenticate the bulb, forcing the user to set it up again to restore its function.
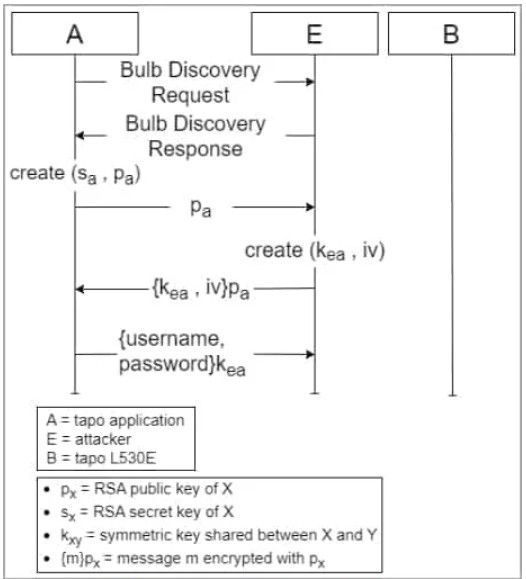
Bulb impersonation diagram (arxiv.org)
Another attack type explored by the researchers is MITM (Man-In-The-Middle) attack with a configured Tapo L530E device, exploiting vulnerability 1 to intercept and manipulate the communication between the app and the bulb and capturing the RSA encryption keys used for subsequent data exchange.
MITM attacks are also possible with unconfigured Tapo devices by leveraging vulnerability one again by connecting to the WiFi during setup, bridging two networks, and routing discovery messages, eventually retrieving Tapo passwords, SSIDs, and WiFi passwords in easily decipherable base64 encoded form.
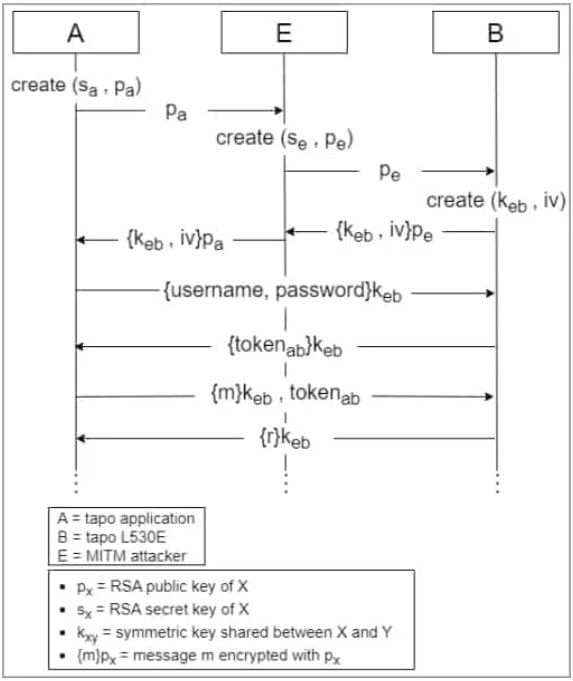
MITM attack diagram (arxiv.org)
Finally, vulnerability 4 allows attackers to launch replay attacks, replicating messages that have been sniffed previously to achieve functional changes in the device.
Disclosure and fixing
The university researchers responsibly disclosed their findings to TP-Link, and the vendor acknowledged them all and informed them they would implement fixes on both the app and the bulb’s firmware soon.
However, the paper does not clarify whether these fixes have already been made available and which versions remain vulnerable to attacks.
BleepingComputer has contacted TP-Link to learn more about the security updates and impacted versions and will update this post as soon as we hear back.
As general advice for IoT security, it is recommended to keep these types of devices isolated from critical networks, use the latest available firmware updates and companion app versions, and protect accounts with MFA and strong passwords.
Source: bleepingcomputer.com
Bạn cũng có thể quan tâm
All Rights Reserved | John&Partners LLC.






