TP-Link fixes critical RCE bug in popular C5400X gaming router
The TP-Link Archer C5400X gaming router is vulnerable to security flaws that could enable an unauthenticated, remote attacker to execute commands on the device.
The TP-Link Archer C5400X is a high-end tri-band gaming router designed to provide robust performance and advanced features for gaming and other demanding applications, and based on the number of user reviews the product has on online stores, it appears to be a popular choice among gamers.
Arbitrary command execution on routers can lead to hijacking routers, data interception, changing DNS settings, and potentially breaching internal networks.
Vulnerability details
The flaw on the TP-Link Archer C5400X is tracked as CVE-2024-5035 (CVSS v4 score: 10.0, “critical”) and was identified by analysts at OneKey through binary static analysis.
The researchers found that the ‘rftest’ binary exposes a network service vulnerable to command injection and buffer overflows on TCP ports 8888, 8889, and 8890.
The ‘rftest’ service runs a network listener on these ports to perform wireless interface self-assessment and related tasks.
An attacker using shell metacharacters can send specially crafted messages to these ports, potentially achieving arbitrary command execution with elevated privileges.
Shell metacharacters are special characters like semicolons, ampersands, and pipes that are used for better function control on command-line shells. However, they can also be abused for command execution when the user input isn’t properly sanitized to prevent unauthorized actions.
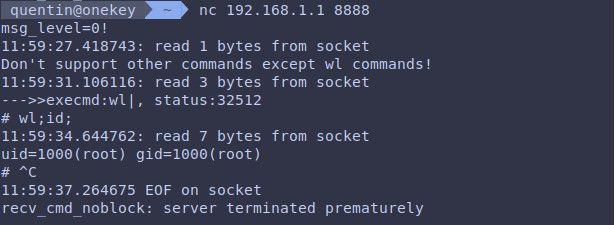
Command ID injection through port 8888
Source: OneKey
Fix available
As the mentioned ports are open and actively used by the ‘rftest’ service on the router’s default configuration, they impact all users of the device using the vulnerable firmware versions, through 1.1.1.6.
OneKey analysts reported their findings to TP-Link’s PSIRT on February 16, 2024, while the vendor had a beta patch ready by April 10, 2024.
Finally, the security update came late last week, on May 24, 2024, with the release of Archer C5400X(EU)_V1_1.1.7 Build 20240510, which effectively addresses CVE-2024-5035.
The implemented fix was to discard any commands containing shell metacharacters, so these are filtered out in all incoming messages.
Users are recommended to download the firmware update from TP-Link’s official download portal or use their router admin panel to perform the update.
Source: bleepingcomputer.com






