‘Sandman’ hackers backdoor telcos with new LuaDream malware
A previously unknown threat actor dubbed 'Sandman' targets telecommunication service providers in the Middle East, Western Europe, and South Asia, using a modular info-stealing malware named 'LuaDream.'
This malicious activity was discovered by SentinelLabs in collaboration with QGroup GmbH in August 2023, who named the threat actor and malware after the backdoor's internal name of 'DreamLand client.'
The operational style of Sandman is to keep a low profile to evade detection while performing lateral movement and maintaining long-term access to breached systems to maximize its cyberespionage operations.
A popular target
The Sandman threat actor targets telecommunication service providers in the Middle East, Western Europe, and South Asia subcontinents.
SentinelOne says the threat actor first gains access to a corporate network using stolen administrative credentials.
Once the network is breached, Sandman has been seen using "pass-the-hash" attacks to authenticate to remote servers and services by extracting and reusing NTLM hashes stored in memory.
The SentinelLabs report explains that, in one instance, all workstations targeted by the hackers were assigned to managerial personnel, indicating the attacker's interest in privileged or confidential information.
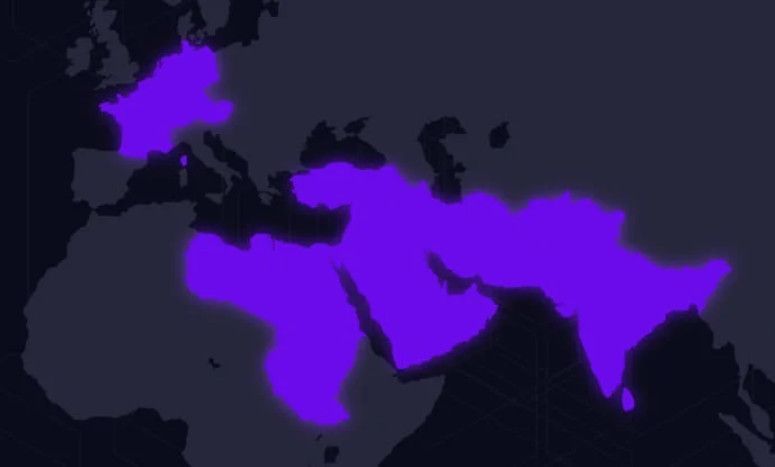
Geographic distribution of Sandman targets
Source: SentinelLabs
LuaDream malware
SandMan has been seen deploying a new modular malware named 'LuaDream' in attacks using DLL hijacking on targeted systems. The malware gets its name from using the LuaJIT just-in-time compiler for the Lua scripting language
The malware is used to collect data and manage plugins that extend its functionality, which are received from the command and control server (C2) and executed locally on the compromised system.
The malware's development appears to be active, with a retrieved version string indicating the release number "12.0.2.5.23.29," and the analysts have seen signs of logs and testing functions going as far back as June 2022.
LuaDream's staging relies on a sophisticated seven-step in-memory process aiming to evade detection, initiated by either the Windows Fax or Spooler service, which runs the malicious DLL file.
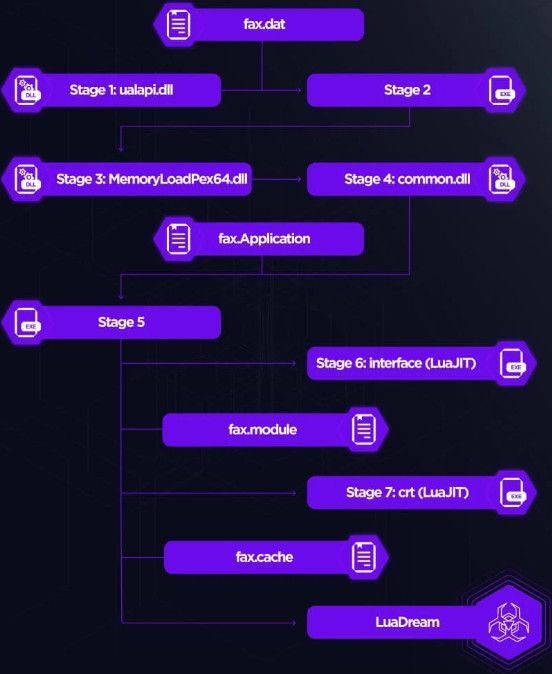
Sandman staging proccess
Source: SentinelLabs
SentinelLabs reports that the timestamps in the DLL files used for order hijacking are very close to the attacks, which might indicate they were custom-created for specific intrusions.
Anti-analysis measures in the staging process include:
- Concealing LuaDream's threads from debuggers.
- Closing files with an invalid handle.
- Detecting Wine-based sandbox environments.
- In-memory mapping to dodge EDR API hooks and file-based detections.
- Packing staging code with XOR-based encryption and compression.
LuaDream comprises 34 components, with 13 core and 21 support components, which utilize the LuaJIT bytecode and the Windows API through the ffi library.
Core components handle the malware's primary functions, like system and user data collection, plugin control, and C2 communications, while support components deal with the technical aspects, like providing Lua libs and Windows API definitions.
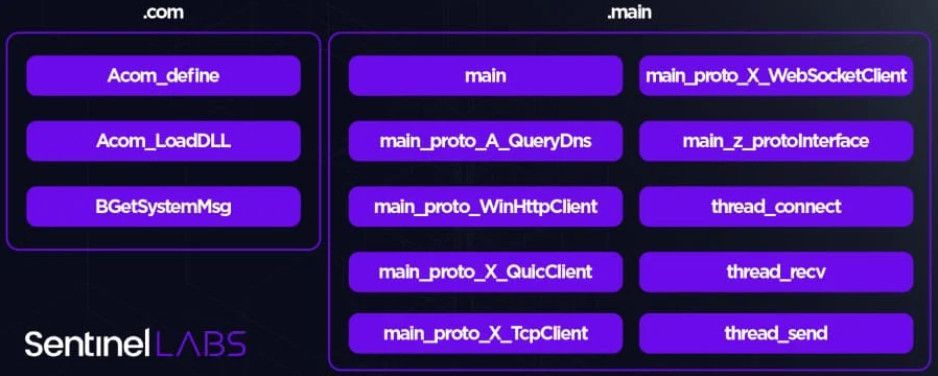
The malware's main components (SentinelLabs)
Upon initialization, LuaDream connects to a C2 server (via TCP, HTTPS, WebSocket, or QUIC) and sends gathered information, including malware versions, IP/MAC addresses, OS details, etc.
Due to the attackers deploying specific plugins through LuaDream in each attack, SentinelLabs doesn't have an exhaustive list of all plugins available.
However, the report notes one module named 'cmd,' whose name suggests it gives the attackers command execution capabilities on the compromised device.
While some of Sandman's custom malware and part of its C2 server infrastructure have been exposed, the threat actor's origin remains unanswered.
Sandman joins a growing list of advanced attackers targeting telecom companies for espionage, using unique stealthy backdoors that are challenging to detect and stop.
Telecommunication providers are a frequent target for espionage activities due to the sensitive nature of the data they manage.
Earlier last week, we reported on a new cluster of activity tracked as 'ShroudedSnooper' that used two novel backdoors, HTTPSnoop and PipeSnoop, against telecommunication carriers in the Middle East.
Source: bleepingcomputer.com
Bạn cũng có thể quan tâm
All Rights Reserved | John&Partners LLC.






