You see QR codes just about everywhere these days. QR code scanning images for medical declaration are everywhere. The pandemic fueled a surge in the use of QR codes. By scanning the small square barcode, you can quickly access a website full of information, from advertisements, to restaurant menus, or online payments.
Cybercriminals quickly took note and are starting to exploit the technology's undeniable convenience. Scammers are creating their own malicious QR codes designed to dupe unwitting consumers into handing over their banking or personal information.
"Anytime new technology comes out, cybercriminals try to find a way to exploit it," said Angel Grant, vice president of security at F5, an app security company. That's especially true with tech like QR codes, which people know how to use but might not know how they work, she says. "It's easier to manipulate people if they don't understand it."
QR codes -- the abbreviation stands for "quick response" -- were invented in Japan in the 1990s. They were first used by the automotive industry to manage production but have spread everywhere. Websites and apps have cropped up that let you make your own.
Like any other phishing scheme, it's impossible to know exactly how often QR codes are used for malicious purposes. Experts say they still represent a small percentage of overall phishing, but numerous scams involving QR code have been reported to the Better Business Bureau, especially in the past year.
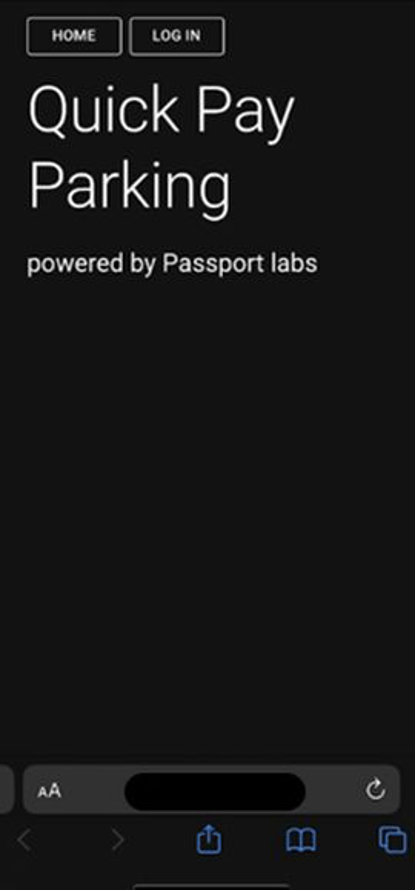
A screenshot of the scam website drivers were led to when they used their phones to scan malicious QR code stickers on parking meters in Austin, Texas.
Austin Transportation
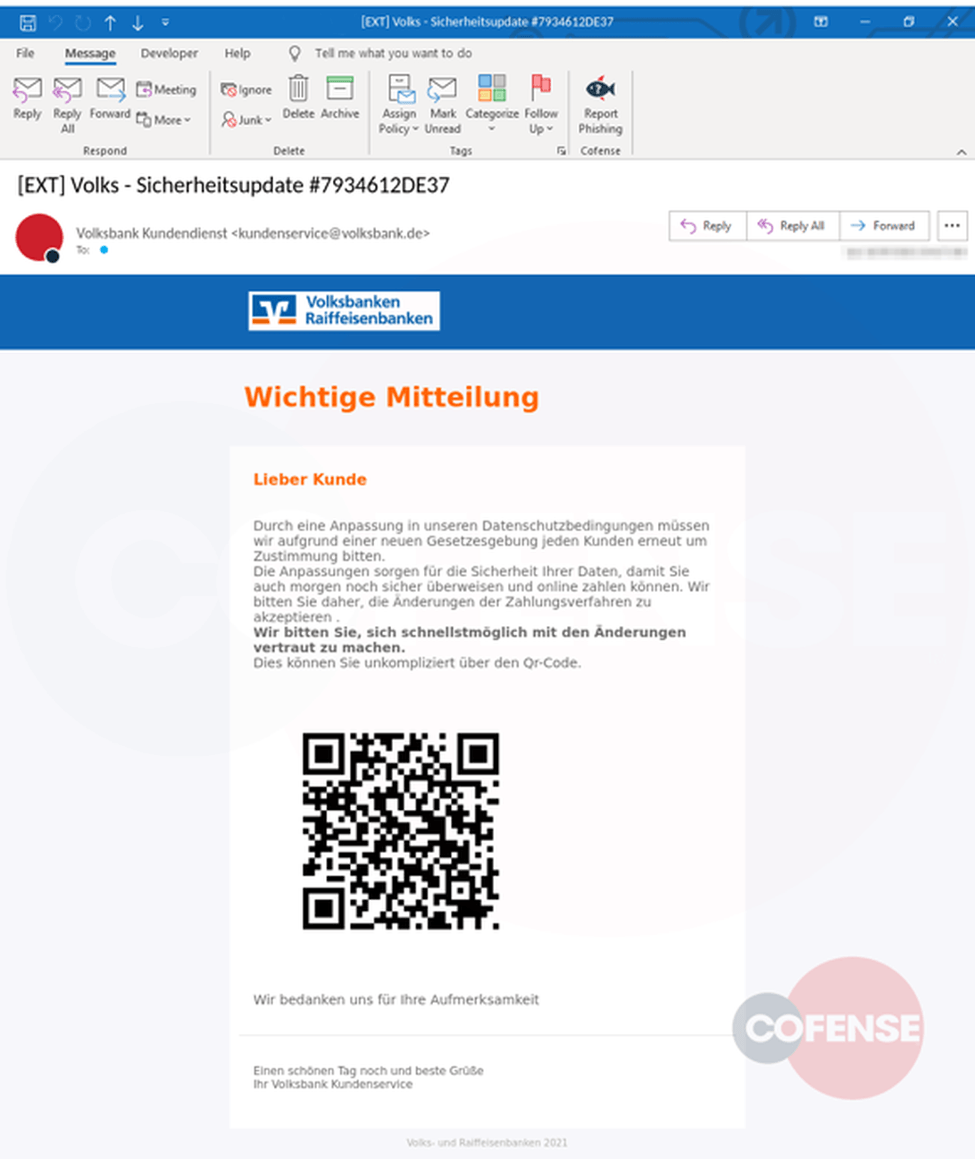
Still, the phony codes show up in phishing emails, though not as often as tried-and-true tactics, like attachments containing viruses or links to scam websites. Cofense recently spotted a phishing scam targeting German speakers that included a QR code in an attempt to lure mobile banking users.
A screenshot of a phishing email containing a malicious QR code spotted by Cofense researchers. Note that the QR code has been altered and will not lead to a malicious website.
Cofense
Hackers may like using QR codes in phishing emails because they often aren't picked up by security software, giving them a better chance to reach their intended targets than attachments or bad links, says Aaron Ansari, vice president for cloud security at the antivirus company Trend Micro.
Even if the success rate is lower, it's a lot easier to send out millions of phishing emails than it is to physically place stickers on parking meters and bus stops.
What it boils down to is that QR codes are just one more way for cybercriminals to get what they want and yet another threat people need to be on the lookout for.
Tips from the experts
Think before you scan.
Be especially wary of codes posted in public places. Take a good look. Is it a sticker or part of a bigger sign or display? If the code doesn't look like it fits in with the background, ask for a paper copy of the document you're trying to access or type the URL in manually.
When you do scan a QR code, take a good look at the website it led you to, Haas recommends. Does it look like you expected it would? If it asks for login or banking information that doesn't seem needed, don't hand it over.
Codes embedded in emails are almost always a bad idea.
Take Haas' advice and skip these entirely. The same goes for codes you receive in unsolicited paper junk mail, such as those offering help with debt consolidation, Grant says.
Preview the code's URL.
Many smartphone cameras, including iPhones running the latest version of iOS, will give you a preview of a code's URL as you start to scan it. If the URL looks strange, you might want to move on.
Better yet, Ansari recommends using a secure scanner app, which is designed to spot malicious links before your phone opens them. Stick to the well-known security companies. Malicious QR scanning apps designed to scrape user information have made it into the app stores in the past.
Use a password manager.
As with all kinds of phishing, if a QR code takes you to an especially convincing fake website, a password manager will still know the difference and won't autofill your passwords, Haas says.
Source: cnet.com