Qilin ransomware claims attack on automotive giant Yanfeng
The Qilin ransomware group has claimed responsibility for a cyber attack on Yanfeng Automotive Interiors (Yanfeng), one of the world's largest automotive parts suppliers.
Yanfeng is a Chinese automotive parts developer and manufacturer focused on interior components and employs over 57,000 people in 240 locations worldwide.
It sells interior components to General Motors, the Volkswagen Group, Ford, Stellantis (Fiat, Chrysler, Jeep, Dodge), BMW, Daimler AG, Toyota, Honda, Nissan, and SAIC Motor. The company constitutes a crucial part of the supply chain for these automakers.
Earlier this month, it was reported that Yanfeng was impacted by a cyberattack that directly affected Stellantis, forcing the car company to stop production at its North American plants.
The Chinese company remained unresponsive to inquiries for comments regarding the situation. However, its main website was inaccessible until on November 28th, when it returned online without any statements regarding the outage.
Stellantis told BleepingComputer they suffered a disruption due to an "issue" at an external supplier.
"Due to an issue with an external supplier, production at some of Stellantis' North America assembly plants was disrupted the week of November 13," Stellantis shared in a statement.
"Full production at all impacted plants had resumed by November 16."
Qilin claims the attack
The Qilin ransomware group, also known as "Agenda," claimed the attack on Yanfeng by adding them to their Tor data leak extortion site on November 27th.
The threat actors published multiple samples to prove their alleged access to Yanfeng systems and files, including financial documents, non-disclosure agreements, quotation files, technical data sheets, and internal reports.
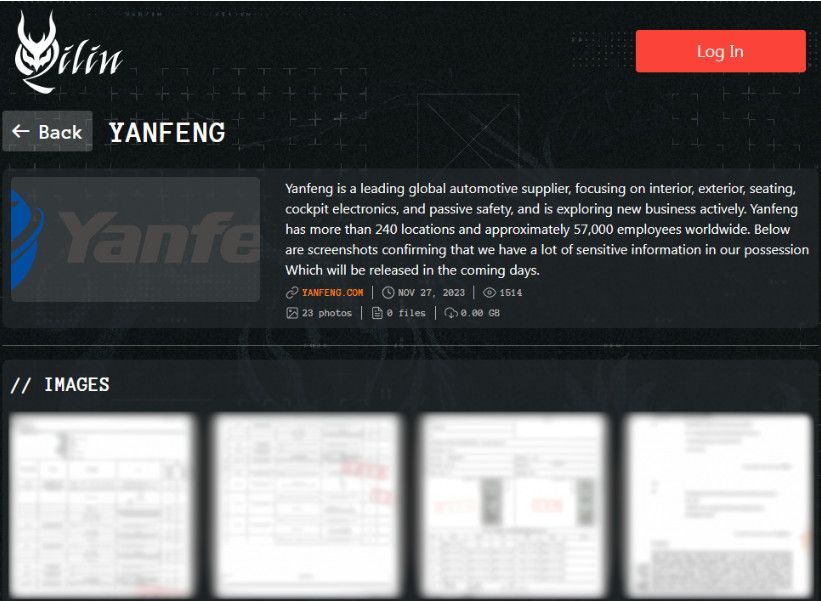
Yanfeng listed on Qilin's extortion portal (BleepingComputer)
Qilin has threatened to release all data in their possession in the coming days, but no specific deadline was set.
The Qilin ransomware gang launched its RaaS (ransomware as a service) platform at the end of August 2022 under the name 'Agenda.'
In 2023, the threat actors rebranded their ransomware under the name 'Qilin,' which they operate under on November 28th.
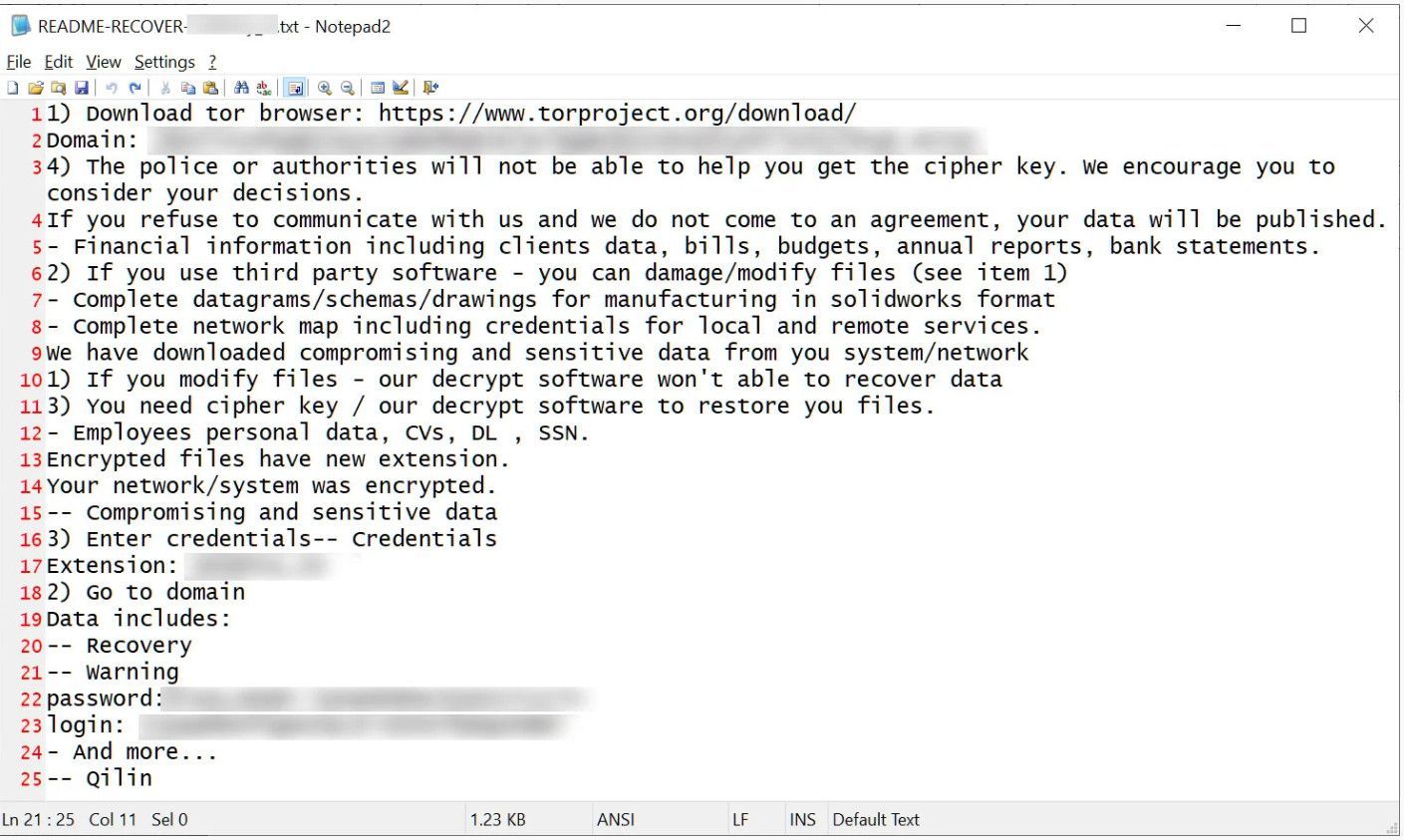
A Qilin ransom note
Source: BleepingComputer
The threat actors target companies in all sectors, and many attacks feature customization in the process termination and file extension changes to maximize impact.
Group-IB managed to infiltrate Qilin’s operations and published a report in May 2023 to share the intelligence it collected, including details about the gang's recruiting, admin panel features, and target exclusions.
Source: BleepingComputer
Bạn cũng có thể quan tâm
All Rights Reserved | John&Partners LLC.






