PyPI suspends new user registration to block malware campaign
The Python Package Index (PyPI) has temporarily suspended user registration and the creation of new projects to deal with an ongoing malware campaign.
PyPI is an index for Python projects that helps developers find and install Python packages.
With thousands of packages available, the repository is an attractive target for threat actors, who often upload typosquatted or fake packages to compromise software developers and potential supply-chain attacks.
Such activity has forced PyPI administrators earlier on March 28 to announce that all new user registrations have been suspended to allow mitigating malicious activity.
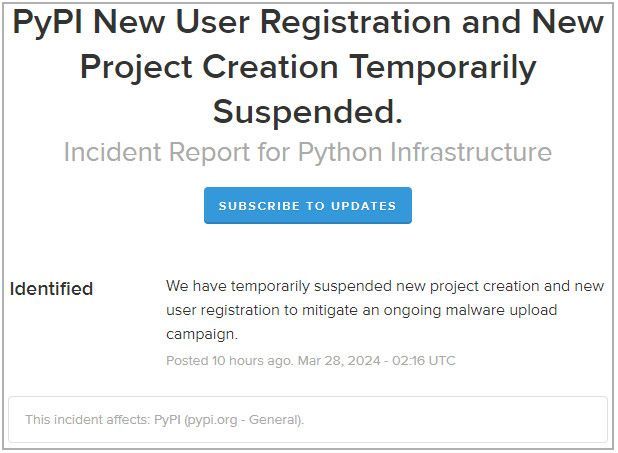
PyPI platform status (BleepingComputer)
Malware campaign
A report from Checkmarx informs that threat actors started yesterday to upload to PyPI 365 packages with names that mimick legitimate projects.
The packages include malicious code within the ‘setup.py’ file that executes upon installation, attempting to retrieve an additional payload from a remote server.
To evade detection, the malicious code is encrypted using the Fernet module, and the remote resource’s URL is dynamically constructed when needed.
The final payload is an info-stealer with persistence capabilities that targets data stored in web browsers, such as login passwords, cookies, and cryptocurrency extensions.
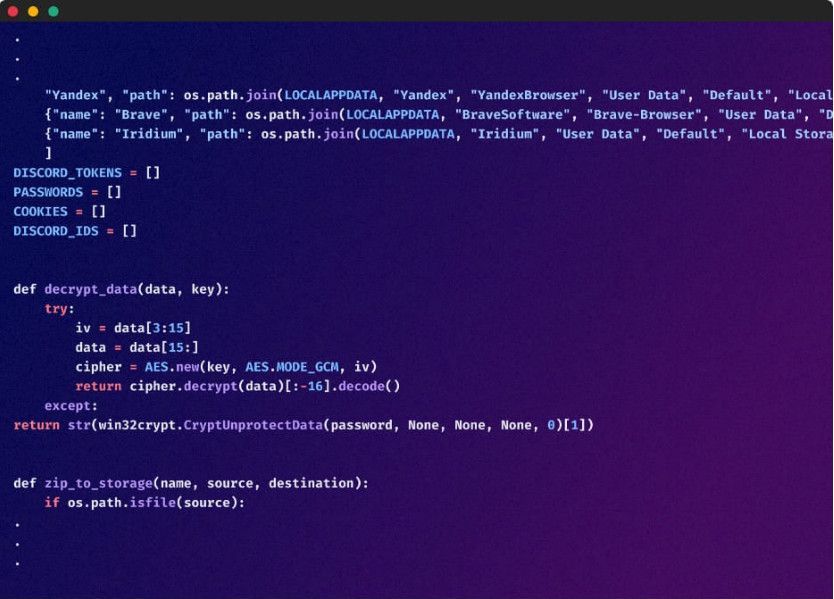
Info-stealer payload (Checkmarx)
Checkmarx makes available in its report the full list of malicious entries they found, which contains numerous typosquatting variants for many legitimate packages.
According to a report from Check Point, though, the list of malicious packages is over 500 and were deployed in two stages. The researchers say that each package originated from unique maintainer accounts with distinct names and emails.
"Notably, each maintainer account uploaded only one package, indicating the utilization of automation in orchestrating the attack," Check Point explains.
The researchers say that all entries had the same version number, contained the same malicious code, and the names appear generated through a randomization process.
This incident underscores the importance of software developers and package maintainers utilizing open-source repositories to rigorously verify the authenticity and security of the components they use in their projects.
This is not the first time PyPI takes such aggressive steps to safeguard its community from malicious submissions. The maintainers of the repository took the same action last year, on May 20.
Source: BleepingComputer
Bạn cũng có thể quan tâm
All Rights Reserved | John&Partners LLC.






