Over 178K SonicWall firewalls vulnerable to DoS, potential RCE attacks
Security researchers have found over 178,000 SonicWall next-generation firewalls (NGFW) with the management interface exposed online are vulnerable to denial-of-service (DoS) and potential remote code execution (RCE) attacks.
These appliances are affected by two DoS security flaws tracked as CVE-2022-22274 and CVE-2023-0656, the former also allowing attackers to gain remote code execution.
"Using BinaryEdge source data, we scanned SonicWall firewalls with management interfaces exposed to the internet and found that 76% (178,637 of 233,984) are vulnerable to one or both issues," said Jon Williams, a Senior Security Engineer at Bishop Fox.
Although the two vulnerabilities are essentially the same as they're caused by reusing the same vulnerable code pattern, they're exploitable at different HTTP URI paths, according to Bishop Fox, who discovered this massive attack surface.
"Our initial research confirmed the vendor's assertion that no exploit was available; however, once we identified the vulnerable code, we discovered it was the same issue announced a year later as CVE-2023-0656," Williams said.
"We found that CVE-2022-22274 was caused by the same vulnerable code pattern in a different place, and the exploit worked against three additional URI paths."
Even if attackers cannot execute code on a targeted appliance, they can exploit vulnerabilities to force it into maintenance mode, requiring intervention from administrators to restore standard functionality.
Thus, even if it's not determined if remote code execution is possible, bad actors could still leverage these vulnerabilities to disable edge firewalls and the VPN access they provide to corporate networks.
More than 500,000 SonicWall firewalls are currently exposed online, with over 328,000 in the United States, according to data from threat monitoring platform Shadowserver.
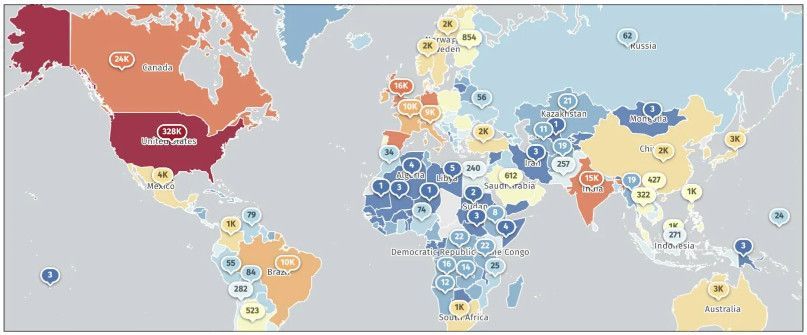
Internet-exposed SonicWall firewalls (ShadowServer)
While the SonicWall Product Security Incident Response Team (PSIRT) says it has no knowledge that these vulnerabilities have been exploited in the wild, at least one proof-of-concept (PoC) exploit is available online for CVE-2022-22274.
"SSD Labs had published a technical writeup of the bug with a proof of concept, noting two URI paths where the bug could be triggered," Williams said.
Admins are advised to ensure their SonicWall NGFW appliances' management interface is not exposed online and upgrade to the latest firmware versions as soon as possible.
SonicWall's appliances have previously been targeted in cyber-espionage attacks and by multiple ransomware gangs, including HelloKitty and FiveHands).
For instance, last March, SonicWall PSIRT and Mandiant revealed that suspected Chinese hackers installed custom malware on unpatched SonicWall Secure Mobile Access (SMA) appliances for long-term persistence in cyber-espionage campaigns.
Customers were also warned in July to urgently patch multiple critical authentication bypass flaws in the company's GMS firewall management and Analytics network reporting products.
SonicWall's customer list includes over 500,000 businesses from more than 215 countries and territories, including government agencies and some of the largest companies worldwide.
Source: bleepingcomputer.com
Bạn cũng có thể quan tâm
All Rights Reserved | John&Partners LLC.






