North Korean hackers exploit critical TeamCity flaw to breach networks
Microsoft says that the North Korean Lazarus and Andariel hacking groups are exploiting the CVE-2023-42793 flaw in TeamCity servers to deploy backdoor malware, likely to conduct software supply chain attacks.
TeamCity is a continuous integration and deployment server organizations use as part of their software development infrastructure.
In September, TeamCity fixed a critical 9.8/10 vulnerability tracked as CVE-2023-42793 that allowed unauthenticated attackers to remotely execute code.
While TeamCity quickly fixed the vulnerability, threat actors, such as ransomware gangs, began to exploit the flaw to breach corporate networks.
North Korean hackers exploit TeamCity
In a new report, Microsoft's Threat intelligence team says that the Lazarus (aka Diamond Sleet and ZINC) and Andariel (aka Onyx Sleet and PLUTONIUM) hacking groups have been observed exploiting CVE-2023-42793 to breach TeamCity servers.
While Microsoft has not said the ultimate goal of these attacks, they believe it could be to conduct software supply chain attacks.
"In past operations, Diamond Sleet and other North Korean threat actors have successfully carried out software supply chain attacks by infiltrating build environments," explains Microsoft.
"Given this, Microsoft assesses that this activity poses a particularly high risk to organizations who are affected. "
Once the threat actors breach a TeamCity server, they utilize different attack chains to deploy backdoors and gain persistence on the compromised network.
Lazarus was seen deploying the ForestTiger malware in one attack chain, which is used as a backdoor for executing commands on the breached server.
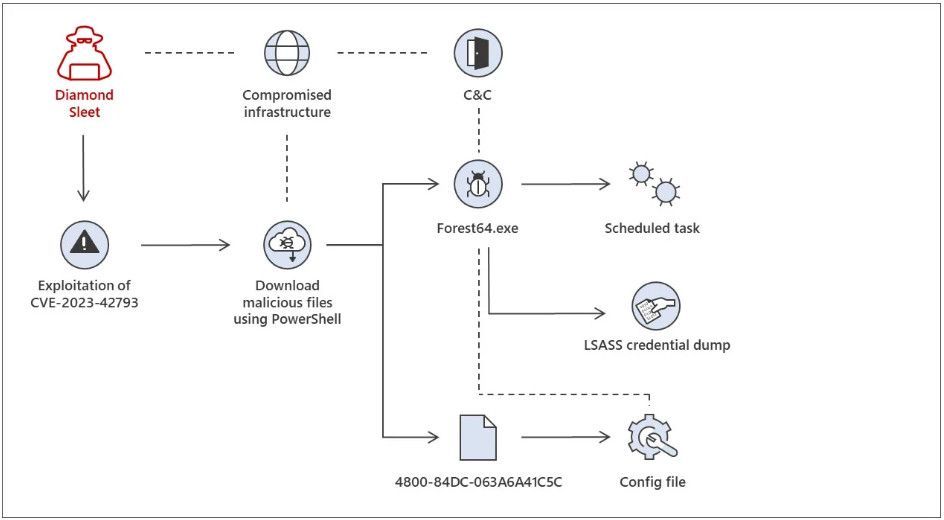
A Lazarus attack chain was seen after exploiting the TeamCity flaw
Source: Microsoft
A second attack chain uses DLL search order hijacking attacks to launch a malware loader called FeedLoad, which installs a remote access Trojan (RAT).
Andariel uses a more hands-on approach in their attacks, creating a 'krtbgt' admin account on the breached server and running commands to gather system information.
The threat actors ultimately deploy a payload that installs the HazyLoad proxy tool, allowing a persistent connection between the compromised server and Andarial's servers.
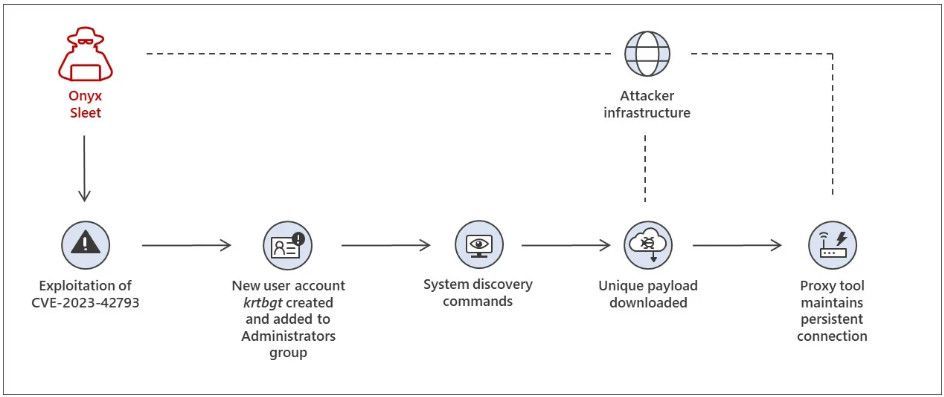
Andariel attack chain seen in breaches
Source: Microsoft
Regardless of how the attacks are conducted, Microsoft says that the hackers ultimately dump credentials from LSASS, likely used to spread laterally on the compromised network.
Microsoft has shared more technical details for all three of the observed attack chains, including indicators of compromise.
Who is Lazarus and Andariel
Both Lazarus and Andariel are state-sponsored North Korean hacking groups, with Andariel a subgroup of Lazarus
While the groups' attacks are used to benefit the North Korean government, their goals can be different.
Lazarus has been linked to various espionage, data theft, and financial gain attacks, including targeting security researchers, trojanizing open-source crypto platforms, performing massive cryptocurrency heists, and conducting fake job interviews to distribute malware.
On the other hand, Andariel targets defense and IT services entities in South Korea, the United States, and India to conduct cyber espionage, data theft, destructive attacks, and ransomware attacks.
The group is known to utilize vulnerabilities for initial access to corporate networks.
Source: bleepingcomputer.com
Bạn cũng có thể quan tâm
All Rights Reserved | John&Partners LLC.






