New MetaMask phishing campaign uses KYC lures to steal passphrases
A new phishing campaign is targeting users on Microsoft 365 while spoofing the popular MetaMask cryptocurrency wallet provider and attempting to steal recovery phrases.
MetaMask recovery phrases, or seeds, are a series of 12 words that users can use to import an existing crypto wallet on other devices. Whoever has access to this recovery phrase can import the wallet on any device they choose and steal the NFTs and cryptocurrency stored within it, making them a popular target for threat actors.
According to email security firm Armorblox the new campaign targets users of Microsoft Office 365, distributing messages that resemble legitimate identity verification requests.
Impersonating MetaMask support
The phishing email, appearing to be sent from MetaMask support, spoofs a Know Your Customer (KYC) verification request and features convincing branding and no typos or other obvious scam giveaways.
KYC requests are part of standard anti-money laundering legal obligations financial companies must abide by, so receiving a request would not necessarily be unusual.
While the real MetaMask doesn’t require its users to verify or provide KYC details, dealing with verification requests can be a frustrating experience, possibly causing recipients to be less cautious.
Interestingly, the phishing actors even give the recipients a comfortable deadline of up to a whole month to take action to verify themselves, which is another false sign of legitimacy as phishing attempts usually involve urgency.
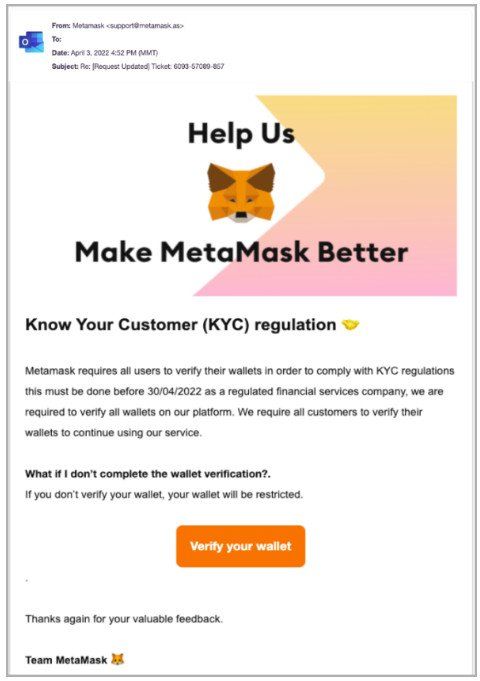
Phishing email used in the campaign (Armorblox)
If the victims click the embedded button, they are taken to a fake landing page crafted to look like the actual MetaMask website.
The phishing site even warns the visitors to ensure that their passphrase is always adequately protected.
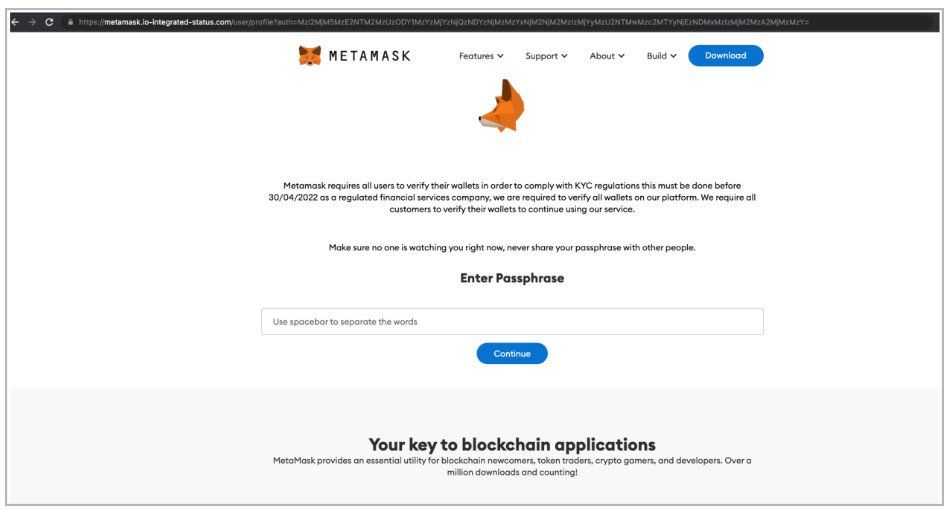
MetaMask phishing site (Armorblox)
The actual MetaMask domain is “metamask.io,” whereas the phishing page uses “metamask.io-integrated-status.com,” which could pass as genuine to unsuspecting users.
If victims enter their passphrase on the phishing site, it goes straight to the threat actors, and often, it doesn’t take long for the adversaries to take action and steal the victim's available funds and NFTs.
How to stay safe
When receiving emails that make serious claims about the status of your accounts, ignore the embedded buttons or provided URLs and instead visit the platform directly from a new tab, login to your account, and check for any alerts requiring your attention.
Remember always to verify the domain you’re about to enter credentials is the correct one, and never jump into action no matter what emergency, or sense of urgency, is presented to you.
Finally, always enable multi-factor authentication (MFA) on all online accounts where the security measure is offered as an option.
Source: bleepingcomputer.com
Bạn cũng có thể quan tâm
All Rights Reserved | John&Partners LLC.






