MOVEit Transfer customers warned of new flaw as PoC info surfaces
Progress warned MOVEit Transfer customers to restrict all HTTP access to their environments after info on a new SQL injection (SQLi) flaw (tracked as CVE-2023-35708) was shared online June 15.
The company has released security patches to address this new critical vulnerability for all affected software versions.
"Progress has discovered a vulnerability in MOVEit Transfer that could lead to escalated privileges and potential unauthorized access to the environment," Progress said.
"All MOVEit Transfer customers must take action and apply the patch to address the June 15th CVE-2023-35708 vulnerability discovered in MOVEit Transfer."
"We have taken HTTPs traffic down for MOVEit Cloud in light of the newly published vulnerability and are asking all MOVEit Transfer customers to immediately take down their HTTP and HTTPs traffic to safeguard their environments while the patch is finalized," the company added.
Until vulnerable servers are patched, Progress "strongly" recommends modifying firewall rules to deny HTTP and HTTPs traffic to MOVEit Transfer on ports 80 and 443 as a temporary workaround.
Even though users would no longer be able to log into their accounts via the web UI, file transfers will still be available since the SFTP and FTP/s protocols will continue to work as expected.
Admins can also access MOVEit Transfer by connecting to the Windows server via remote desktop and then going to https://localhost/.
While Progress didn't share the location where details on this new SQLi flaw were shared, at least one security researcher has shared information on Twitter on what looks like proof-of-concept exploit code for a new MOVEit Transfer zero-day bug.
The researcher told BleepingComputer that they believe this new warning from Progress is related to the PoC they are working on.
"I have not achieved RCE. This vulnerability is not a bypass of any previous vulnerability. It has its own attack path," the researcher added.
BleepingComputer was also told that the vulnerability had already been disclosed to Progress with the help of Huntress Senior Security Researcher John Hammond—the disclosure likely also prompted the company's warning.
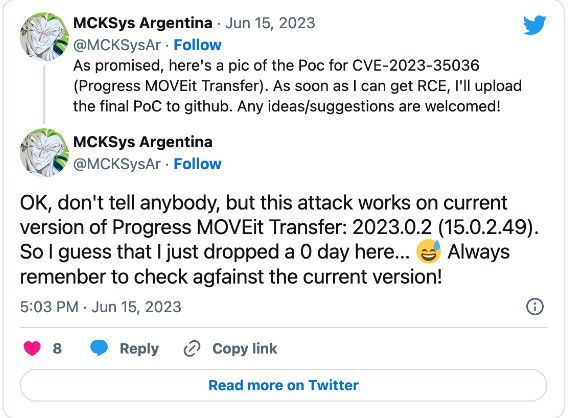
June 15's warning follows another advisory published on June 9 that disclosed critical SQL injection vulnerabilities collectively tracked as CVE-2023-35036 and discovered following a security audit initiated on May 31, when Progress issued patches for a flaw (CVE-2023-34362) exploited as a zero-day by the Clop ransomware gang in data theft attacks.
CVE-2023-35036 impact all MOVEit Transfer versions and let unauthenticated attackers compromise unpatched and Internet-exposed servers to steal customer information.
The Clop ransomware gang claimed responsibility for the CVE-2023-34362 attacks and told BleepingComputer that they allegedly breached the MOVEit servers of "hundreds of companies."
Kroll also found evidence that Clop has been testing exploits for the now-patched MOVEit zero-day since 2021 and ways to exfiltrate data stolen from compromised MOVEit servers since at least April 2022.
Clop has been linked to other wide-impact campaigns targeting managed file transfer platforms, including the breach of Accellion FTA servers in December 2020, SolarWinds Serv-U Managed File Transfer attacks in 2021, and widespread exploitation of GoAnywhere MFT servers in January 2023.
Affected orgs already being extorted
On June 14, the Clop gang started extorting organizations impacted by the MOVEit data theft attacks by listing their names on its dark web data leak site.
Five of the listed companies—British multinational oil and gas company Shell, the University of Georgia (UGA) and University System of Georgia (USG), UnitedHealthcare Student Resources (UHSR), Heidelberger Druck, and Landal Greenparks—have since confirmed to BleepingComputer that they were impacted in the attacks.
Other organizations that have already disclosed MOVEit Transfer breaches include Zellis (and its customers BBC, Boots, Aer Lingus, and Ireland's HSE), Ofcam, the government of Nova Scotia, the US state of Missouri, the US state of Illinois, the University of Rochester, the American Board of Internal Medicine, BORN Ontario, and Extreme Networks.
June 15, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) also revealed that several U.S. federal agencies had been breached, per a CNN report. Two U.S. Department of Energy (DOE) entities were also compromised, according to Federal News Network.
Update June 16, 09:54 EDT: Progress has released patches for the newly discovered vulnerability tracked as CVE-2023-35708.
Source: bleepingcomputer.com
Bạn cũng có thể quan tâm
All Rights Reserved | John&Partners LLC.






