Microsoft: New malware uses Windows bug to hide scheduled tasks
Microsoft has found a new malware used by the Chinese-backed Hafnium hacking organization to create and hide scheduled tasks on compromised Windows Systems in order to sustain persistence.
Cyberespionage attacks by the Hafnium threat group have previously targeted US defense businesses, think tanks, and researchers. It's also one of the state-sponsored organisations Microsoft has tied to the global exploitation of the ProxyLogon zero-day vulnerability, which affected all supported Microsoft Exchange versions last year.
Persistence via Windows registry value removal
"As Microsoft continues to track the high-priority state-sponsored threat actor HAFNIUM, new activity has been uncovered that leverages unpatched zero-day vulnerabilities as initial vectors," the Microsoft Detection and Response Team (DART) said.
"Further investigation reveals forensic artifacts of the usage of Impacket tooling for lateral movement and execution and the discovery of a defense evasion malware called Tarrask that creates 'hidden' scheduled tasks, and subsequent actions to remove the task attributes, to conceal the scheduled tasks from traditional means of identification."
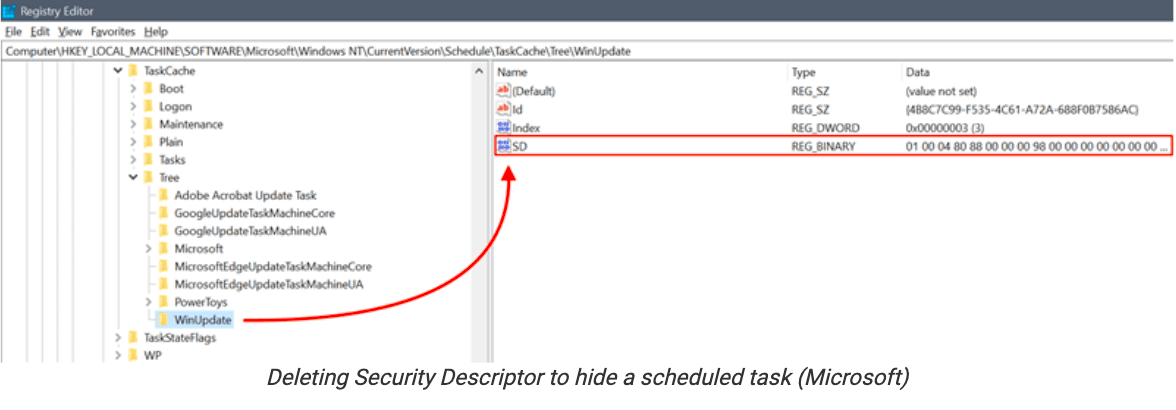
This hacking tool, dubbed Tarrask, uses a previously unknown Windows bug to hide them from "schtasks /query" and Task Scheduler by deleting the associated Security Descriptor registry value. The threat group used these "hidden" scheduled tasks to maintain access to the hacked devices even after reboots by re-establishing dropped connections to command-and-control (C2) infrastructure.
While the Hafnium operators could have removed all on-disk artifacts, including all registry keys and the XML file added to the system folder to delete all traces of their malicious activity, it would have removed persistence across restarts.
How to defend against Tarrask attacks
The "hidden" tasks can only be found upon closer manual inspection of the Windows Registry if you look for scheduled tasks without an SD (security descriptor) Value within their Task Key. Admins can also enable the Security.evtx and the Microsoft-Windows-TaskScheduler/Operational.evtx logs to check for key events linked to tasks "hidden" using Tarrask malware.
Microsoft also recommends enabling logging for 'TaskOperational' within the Microsoft-Windows-TaskScheduler/Operational Task Scheduler log and monitoring for outbound connections from critical Tier 0 and Tier 1 assets.
"The threat actors in this campaign used hidden scheduled tasks to maintain access to critical assets exposed to the internet by regularly re-establishing outbound communications with C&C infrastructure," DART added.
"We recognize that scheduled tasks are an effective tool for adversaries to automate certain tasks while achieving persistence, which brings us to raising awareness about this oft-overlooked technique."
Source: BleepingComputer
Bạn cũng có thể quan tâm
All Rights Reserved | John&Partners LLC.






