Hackers target Check Point VPNs to breach enterprise networks
Threat actors are targeting Check Point Remote Access VPN devices in an ongoing campaign to breach enterprise networks, the company warned in a May 27 advisory.
Remote Access is integrated into all Check Point network firewalls. It can be configured as a client-to-site VPN for access to corporate networks via VPN clients or set up as an SSL VPN Portal for web-based access.
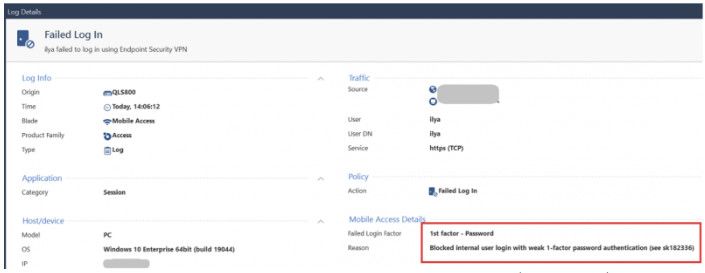
Check Point says the attackers are targeting security gateways with old local accounts using insecure password-only authentication, which should be used with certificate authentication to prevent breaches.
"We have recently witnessed compromised VPN solutions, including various cyber security vendors. In light of these events, we have been monitoring attempts to gain unauthorized access to VPNs of Check Point's customers. By May 24, 2024 we identified a small number of login attempts using old VPN local-accounts relying on unrecommended password-only authentication method," the company said.
"We've seen 3 such attempts, and later when we further analysed it with the special teams we assembled, we saw what we believe are potentially the same pattern (around the same number). So - a few attempts globally all in all but enough to understand a trend and especially- a quite straightforward way to ensure it’s unsuccessful," a Check Point spokesperson told BleepingComputer.
To defend against these ongoing attacks, Check Point warned customers to check for such vulnerable accounts on Quantum Security Gateway and CloudGuard Network Security products and on Mobile Access and Remote Access VPN software blades.
Customers are advised to change the user authentication method to more secure options (using instructions in this support document) or delete vulnerable local accounts from the Security Management Server database.
The company has also released a Security Gateway hotfix that will block all local accounts from authenticating with a password. After installation, local accounts with weak password-only authentication will be prevented from logging into the Remote Access VPN.
Vulnerable local account blocked after installing the hotfix (Check Point)
Customers can find more information on improving their VPNs' security in this support article, which also shares guidance on responding to unauthorized access attempts."By May 24th.
Cisco VPN devices also heavily targeted
Check Point is the second company warning its VPN devices are being targeted in ongoing attacks in recent months.
In April, Cisco also warned about widespread credential brute-forcing attacks targeting VPN and SSH services on Cisco, Check Point, SonicWall, Fortinet, and Ubiquiti devices.
That campaign started around March 18, 2024, with the attacks originating from TOR exit nodes and using various other anonymization tools and proxies to evade blocks.
One month earlier, Cisco warned about a wave of password-spraying attacks targeting Cisco Secure Firewall devices running Remote Access VPN (RAVPN) services, likely part of first-stage reconnaissance activity.
Security researcher Aaron Martin linked this activity to an undocumented malware botnet he dubbed "Brutus," which controlled at least 20,000 IP addresses across cloud services and residential networks.
Last month, the company also revealed that the UAT4356 (aka STORM-1849) state-backed hacking group has been using zero-day bugs in Cisco Adaptive Security Appliance (ASA) and Firepower Threat Defense (FTD) firewalls to breach government networks worldwide since at least November 2023 in a cyber-espionage campaign tracked as ArcaneDoor.
Source: bleepingcomputer.com






