Hackers impersonate U.S. government agencies in BEC attacks
A gang of hackers specialized in business email compromise (BEC) attacks and tracked as TA4903 has been impersonating various U.S. government entities to lure targets into opening malicious files carrying links to fake bidding processes.
According to Proofpoint, whose analysts have been tracking the campaign, the threat actors impersonate the U.S. Department of Transportation, the U.S. Department of Agriculture (USDA), and the U.S. Small Business Administration (SBA).
The email security company also reports that the threat actor has been active since at least 2019 but intensified its activities since mid-2023 and through 2024. The latest tactic observed is the use of QR codes in PDF document attachments.

Phony bidding call PDFs (Proofpoint)
The PDFs are themed after the spoofed organization, but follow a consistent design. Also, they all feature the same metadata, including an author name that points to Nigerian origin.
Recipients scanning the QR codes are redirected to phishing sites crafted to resemble the official portals from the impersonated U.S. government agencies.
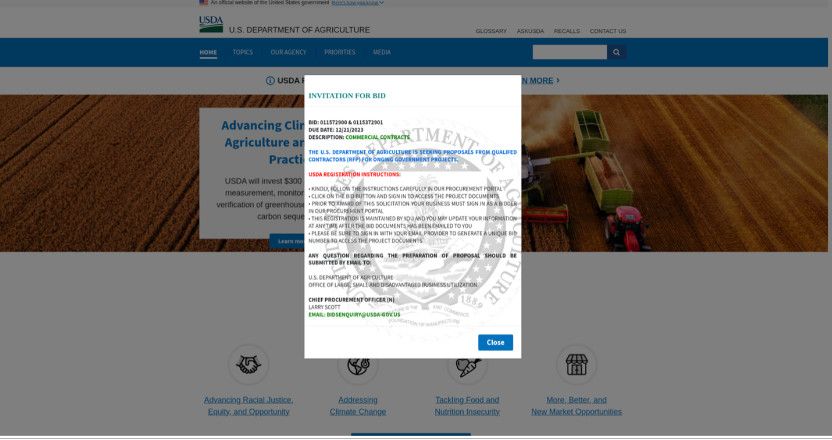
Phishing site impersonating the USDA (Proofpoint)
Depending on the lure in the phishing message, the recipients may be redirected to O365 login pages where they are prompted to enter their credentials.
TA4903 relied in the past on ‘EvilProxy’ to bypass bypass multi-factor authentication (MFA) protection, but Proofpoint notes that the use of the reverse proxy has not been observed this year.
Based on Proofpoint’s observations over time and from tracking the account credentials the company planted on the phishing sites, TA4903's activity is purely financially motivated and includes the following tactics:
- Gaining unauthorized access to corporate networks or email accounts.
- Searching the compromised accounts for keywords related to banking information, payments, or merchants to find opportunities for financial fraud.
- Conducting BEC attacks, such as sending fraudulent payment or invoice requests from the compromised email account to other employees or partners.
In several instances first observed in mid-2023, the threat actor used the theme of a cyberattack in attempts to trick the staff in the financial department into updating payment details.
Those messages were delivered from compromised email accounts of the target’s partner organizations, or addresses that closely resembled them.
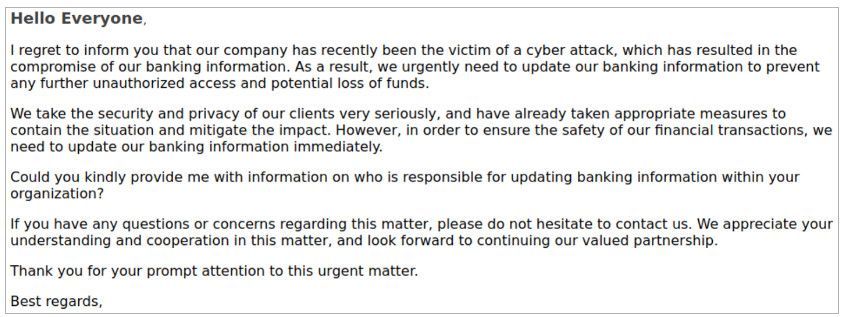
Cyberattack themed message (Proofpoint)
TA4903 represents a significant threat to organizations globally, constantly launching large-scale email campaigns aimed at a wide range of organizations. It typically targets organizations in the U.S. with high-volume email campaigns.
According to Proofpoint, TA4903 is known to register domain names that resemble government entities and private organizations in various sectors.
However, the researchers noticed TA4903 shifting recently from spoofing U.S. government entities to impersonating small businesses, but it is unclear if the switch is temporary or a longer term change.
The complexity of their BEC attacks, which involve multiple steps, provides several opportunities for detection. Therefore, adopting a comprehensive, multi-layered security strategy is the most effective method for mitigating these threats.
Source: bleepingcomputer.com






