HACK
#YOUR FUTURE
John&Partners, LLC. cybersecurity is partnering with best-of-breed in enterprise cybersecurity technology. We are committed to "co-partner" with our network of trusted partners bringing new technologies to the market to transform into a strategic business partnership to tackle Vietnam's challenges.
The objective is by being the first to understand how the new technology works, the trusted partners gain a competitive advantage.
Return on Security Investments.
“A mature cybersecurity program boils down to selecting the right set of security controls, investments, and financial risk mitigations with the board’s approval. Balancing the security budget and the reduced risk is essential to yielding higher returns, or ‘Return on Security Investments.’ That’s why people should lead these initiatives with a business mindset, not just a control or technology mindset.”
Nguyễn Thanh Tú,
John&Partners, LLC. Cybersecurity
Managing Director
Cybersecurity solutions
BODYGUARDS FOR YOUR BUSINESS
Data breaches are making headline news, businesses are going out of business, and the bad guys are getting smarter and sometimes get away scot-free. So, the security of your livelihood is of the utmost importance to us. But we know we can’t do it alone; that’s why our technology partners use Artificial Intelligence and Machine Learning.
Technology is evolving every day, and we must have all the hands-on deck and be innovative to stay ahead of the game. Our local partners specialize in planning, implementing, auditing, monitoring, and managing your entire IT/OT infrastructure while taking all the risks.
John&Partners, LLC. Cybersecurity takes pride to be the exclusive representative in Vietnam of leading cybersecurity technology partners.
Teel Technologies
Chuyên cung cấp các công cụ, máy móc và trang thiết bị pháp y mạng cho phòng thí nghiệm điều tra pháp y an ninh, đào tạo và các dịch vụ tốt nhất cho các chuyên gia điều tra thiết bị di động và phương tiện kỹ thuật số.
Coinfirm
Khi việc sử dụng tiền điện tử tăng lên, rủi ro đối với ngành dịch vụ tài chính cũng tăng theo. Coinfirm dẫn đầu ngành về tuân thủ tiền điện tử, với Nền tảng quản lý rủi ro AML cho tài sản tiền điện tử và blockchain, được các thương hiêu hàng đầu trên toàn thế giới tin cậy.

SEPIO SYSTEMS
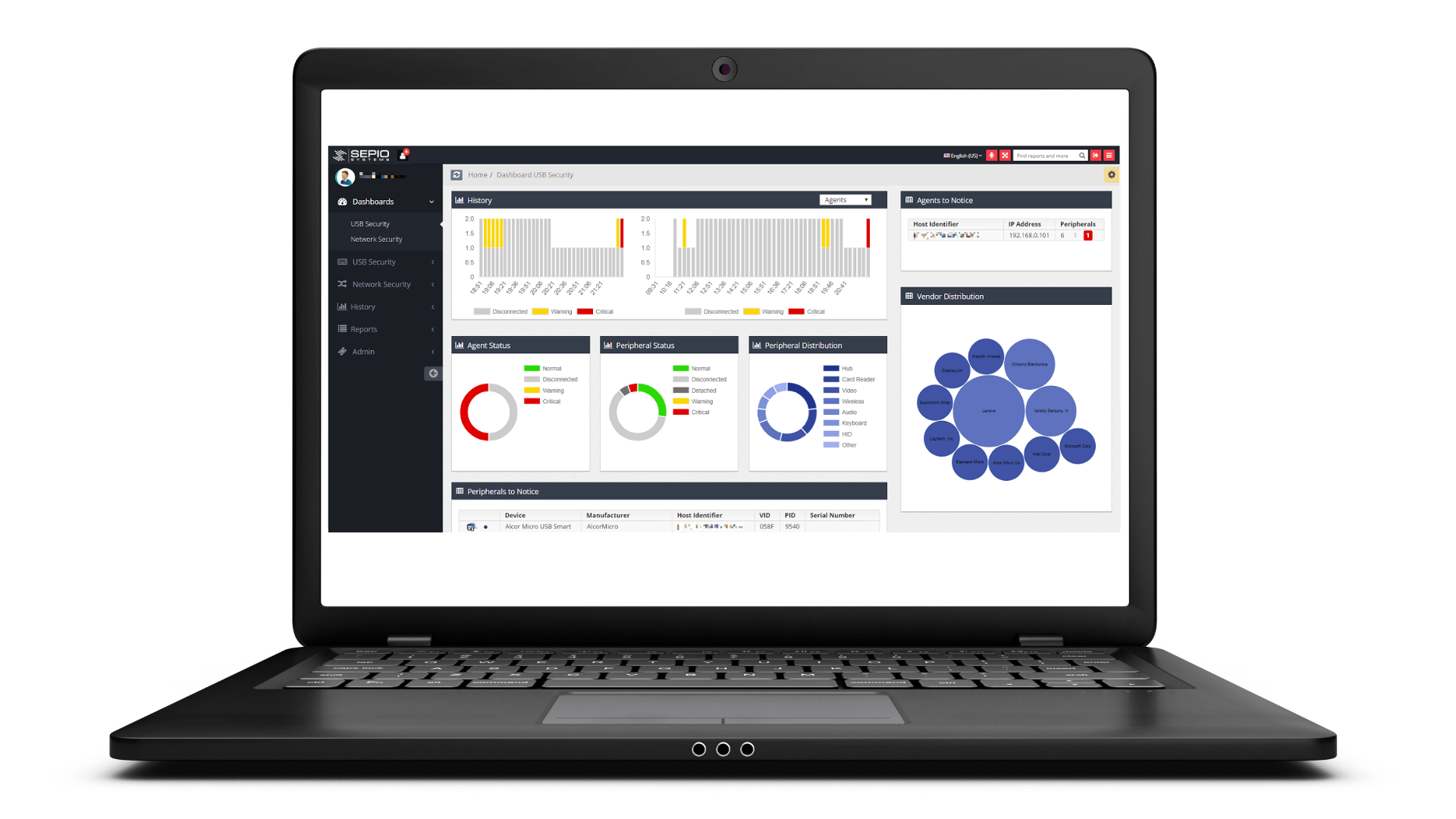
Managing Hardware Related Risks For Enterprises Using Physical Layer (L1) Data
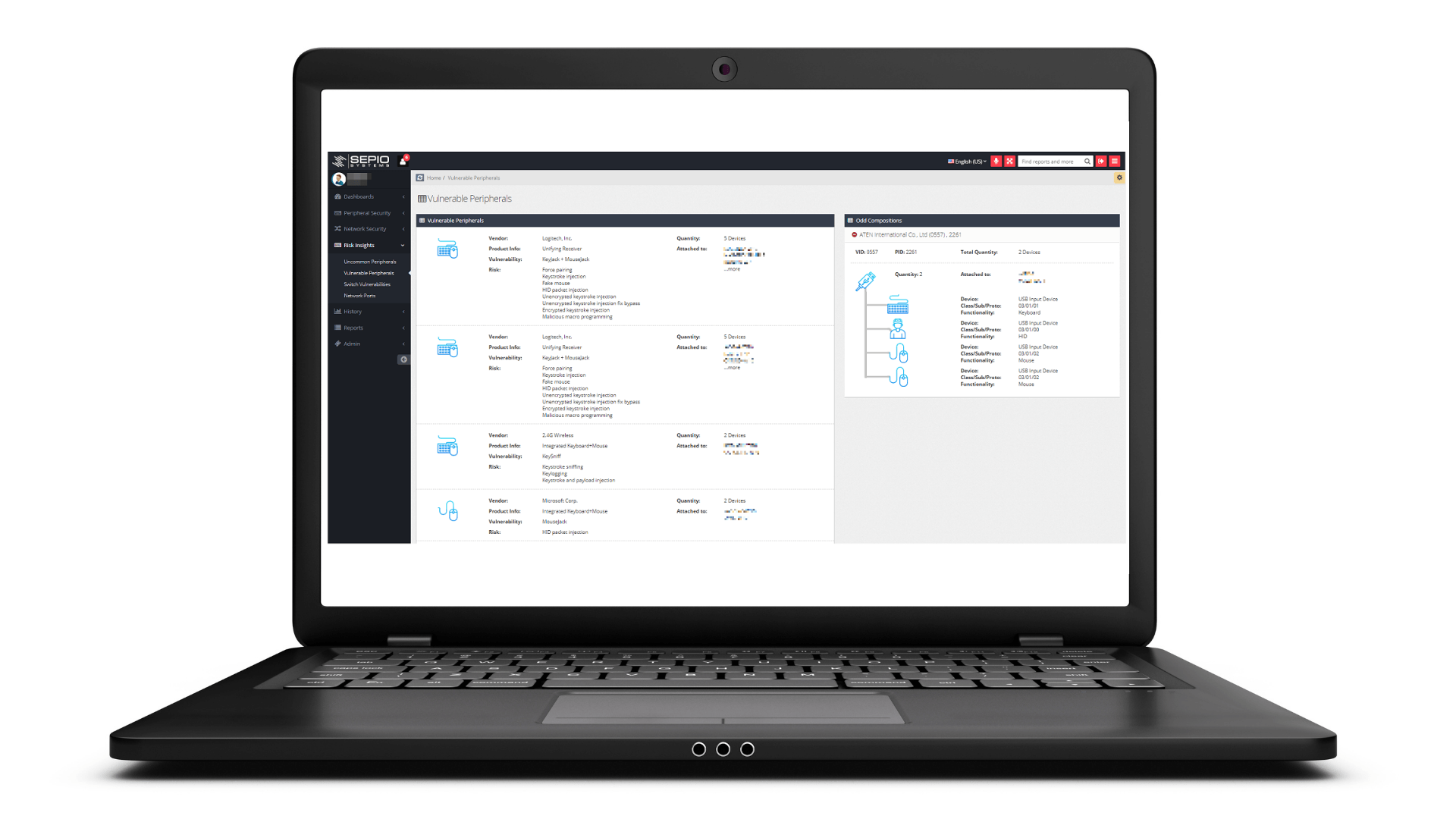
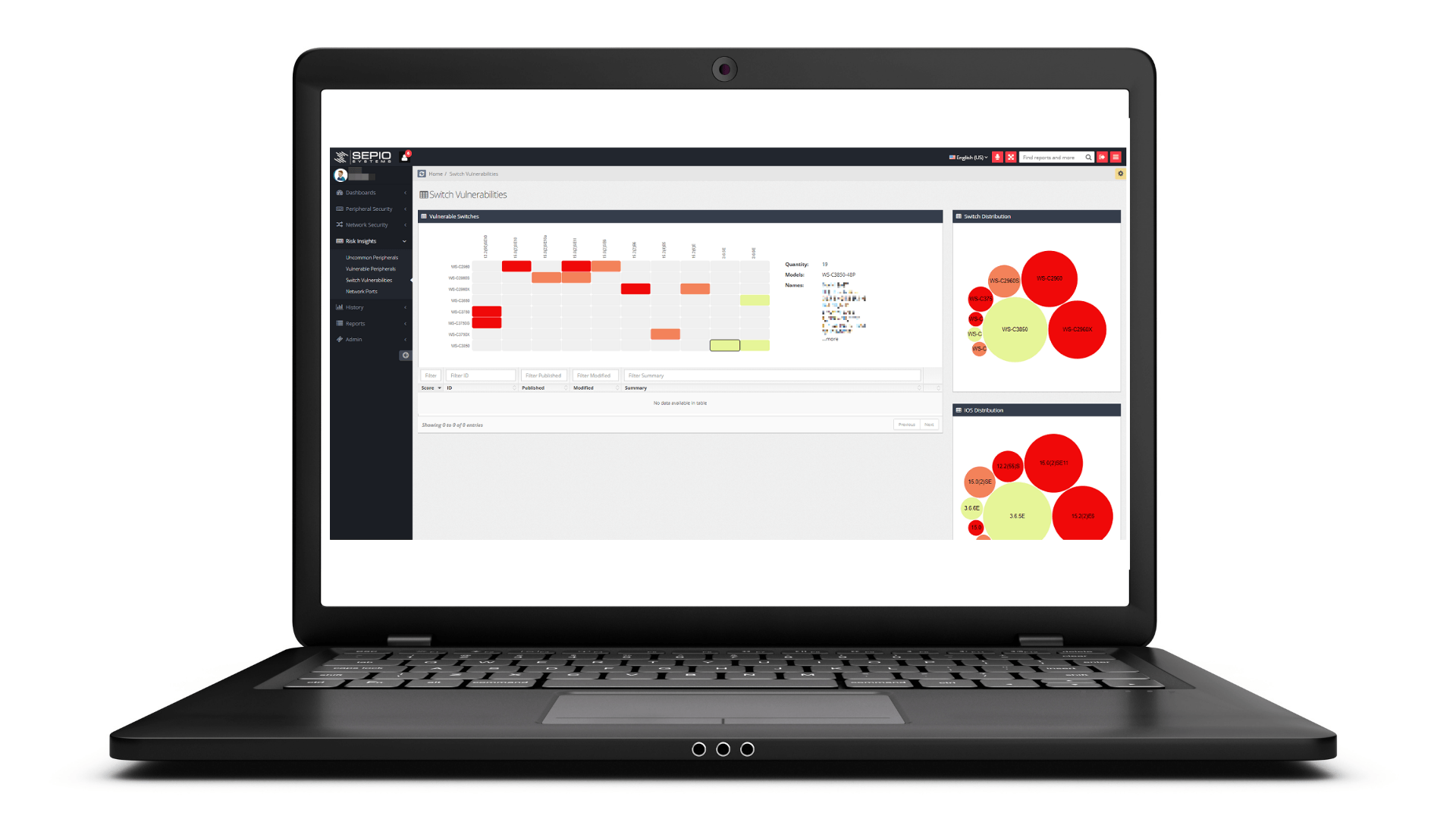
Existing cyber security products do not provide the required visibility level, nor the capability to enforce granular policies. Furthermore, cyber crime organizations and state sponsored activities exploit those “blind spots” to gain access to your organization’s most valuable assets – by injecting malware, ransomware and leaking data through the use of Rogue Devices, which are detected only by Sepio Systems’ physical layer fingerprinting algorithm.
Founded in 2016 by cybersecurity industry veterans from the Israeli Intelligence community, Sepio HAC-1 is the first hardware access control platform that provides visibility, control, and mitigation to zero trust, insider threat, BYOD, IT, OT and IoT security programs. Sepio’s hardware fingerprinting technology discovers all managed, unmanaged and hidden devices that are otherwise invisible to all other security tools. Sepio is a strategic partner of Munich Re, the world’s largest reinsurance company, and Merlin Cyber, a leading cybersecurity federal solution provider.
Key Benefits of Sepio Systems' HAC-1
Complete Visibility
of all Hardware Assets
With all devices and anomalies detected, enterprises benefit from a greater overall cybersecurity posture. Gaining full visibility of all hardware devices from endpoint peripherals to connected devices (IT/OT/IoT), Sepio uses unique physical layer hardware fingerprinting technology and data augmentation from endpoints and networks.
Full Control through
Predefined Policies
Enterprise-wide policies enable compliance, regulation and best practices. With predefined templates and no baselining or whitelisting, and no requirement for a clean environment start, Sepio provides a fast and easy setup.
Rogue Device Mitigation
(RDM)
Threat mitigation upon discovery of rogue or threatening devices. Integrations with existing security platforms such as NACs and SOARs for mitigation and remediation enhancements.