D-Link WiFi range extender vulnerable to command injection attacks
The popular D-Link DAP-X1860 WiFi 6 range extender is susceptible to a vulnerability allowing DoS (denial of service) attacks and remote command injection.
The product is currently listed as available on D-Link's site and has thousands of reviews on Amazon, so it's a popular choice among consumers.
A team of German researchers (RedTeam) who discovered the vulnerability, tracked as CVE-2023-45208, report that despite their attempts to alert D-Link multiple times, the vendor has remained silent, and no fixes have been released.
Vulnerability details
The problem lies in the network scanning functionality of D-Link DAP-X1860, specifically, the inability to parse SSIDs containing a single tick (') in the name, misinterpreting it as a command terminator.
Technically, the problem originates from the 'parsing_xml_stasurvey' function in the libcgifunc.so library, which contains a system command for execution.
However, given the product's lack of SSID sanitization, an attacker can easily abuse this feature for malicious purposes.
An attacker within the extender's range can set up a WiFi network and deceptively name it similar to something the target is familiar with but include a tick in the name, like 'Olaf's Network,' for example.
When the device attempts to connect to that SSID, it will produce an "Error 500: Internal Server Error", failing to operate normally.
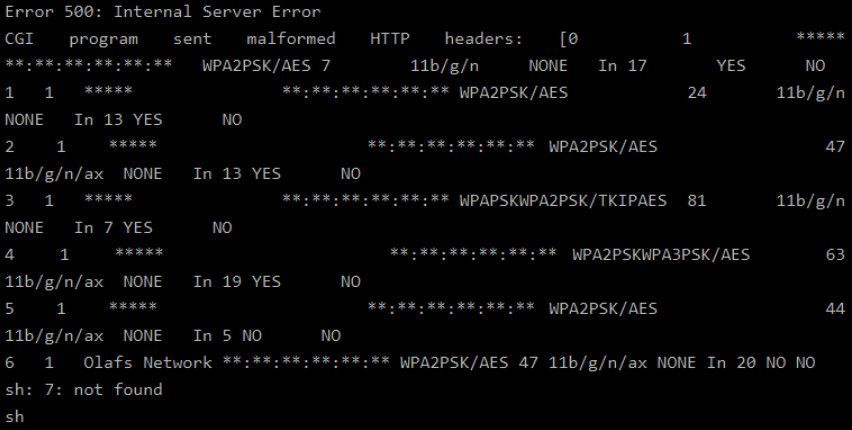
Extender's web server response (RedTeam)
If the attacker adds a second section to the SSID that contains a shell command separated by "&&" like "Test' && uname -a &&", the extender will be tricked to execute the 'uname -a' command upon setup/network scan.
All processes on the extender, including any commands injected by external threat actors, are run with root privileges, potentially allowing the attackers to probe other devices connected to the extender and further their network infiltration.
The hardest prerequisite for the attack is forcing a network scan on the target device, but this is possible by performing a deauthentication attack.
Several readily available software tools can generate and send deauth packets to the extender, causing it to disconnect from its main network and forcing the target to perform a network scan.
RedTeam researchers discovered the flaw in May 2023 and reported it to D-Link, but despite multiple follow-ups, no reply was ever received.
This means that D-Link DAP-X1860 is still vulnerable to attacks, and the relatively simple exploitation mechanism makes the situation risky.
Owners of DAP-X1860 extenders are recommended to limit manual network scans, treat sudden disconnections suspiciously, and turn off the extender when not actively used.
Also, consider placing IoT devices and range extenders on a separate network isolated from sensitive devices holding personal or work data.
Source: bleepingcomputer.com
Bạn cũng có thể quan tâm
All Rights Reserved | John&Partners LLC.






