Bumblebee malware returns in new attacks abusing WebDAV folders
The malware loader 'Bumblebee' has broken its two-month vacation with a new campaign that employs new distribution techniques that abuse 4shared WebDAV services.
WebDAV (Web Distributed Authoring and Versioning) is an extension of the HTTP protocol that enables clients to perform remote authoring operations such as creating, accessing, updating, and deleting web server content.
Intel471's researchers report that Bumblebee's latest campaign, which started on September 7, 2023, abuses the 4shared WebDAV services to distribute the loader, accommodate the attack chain, and perform several post-infection actions.
The abuse of the 4shared platform, a legitimate and well-known file-hosting services provider, helps Bumblebee operators evade blocklists and enjoy high infrastructure availability.
At the same time, the WebDAV protocol gives them multiple ways to bypass behavioral detection systems and the added advantage of streamlined distribution, easy payload switching, etc.
Spam emails
The current Bumblebee campaign relies on malspam emails that pretend to be scans, invoices, and notifications to lure recipients into downloading malicious attachments.
Most attachments are Windows shortcut LNK files, but there are also some ZIP archives containing LNK files, likely a sign that the Bumblebee operators are experimenting to determine what works best.
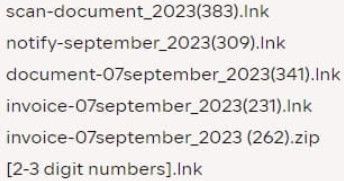
File attachments observed in the campaign (Intel471)
Opening the LNK file launches a series of commands on the victim's machine, starting with one to mount a WebDAV folder on a network drive using hardcoded credentials for a 4shared storage account.
4Shared is a file-sharing site that allows users to store files in the cloud and access them over WebDAV, FTP, and SFTP. The service was previously listed in the US government's 2016 Notorious Markets report for the hosting of copyrighted content.
Here, too, Intel471 spotted several variations of the command set, from mounting the file copies, extracting, and executing the files from the mounted drive, which is another indication of trial for optimization.
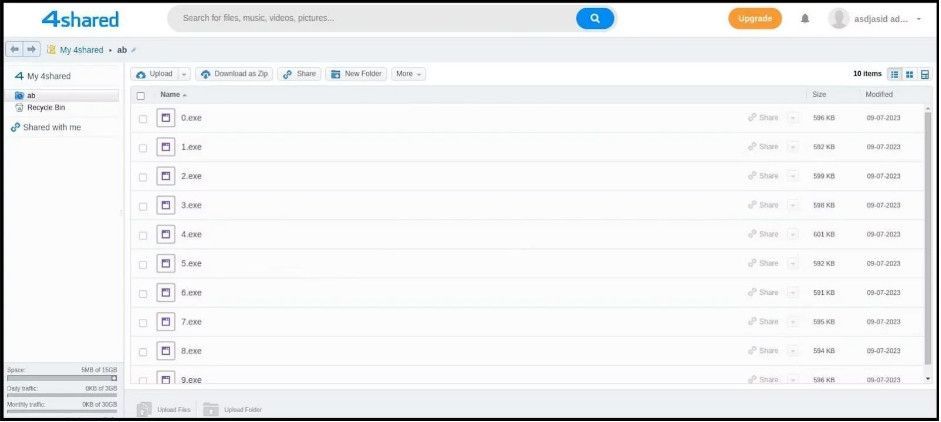
Malicious payloads hosted on 4shared (Intel471)
Intel471 reports seeing the threat actors experimenting with different methods for mounting file copies, extracting, and executing files from the mounted drive, indicating they are trying to optimize the attack chain.
New Bumblebee
The analysts have also spotted an updated version of the Bumblebee malware loader being used in this campaign, which has switched from using the WebSocket protocol to TCP for command and control server (C2) communications.
Additionally, the new loader has abandoned the use of hardcoded C2 addresses. It now uses a domain generation algorithm (DGA) to generate 100 domains on the ".life" top-level domain (TLD) space upon execution.
The domains are generated using a 64-bit static seed value, and Bumblebee connects to them by iterating through the created list until it finds one that resolves to an active C2 server IP address.
Bumblebee has been previously associated with ransomware payload distribution, including Conti and Akira, so adopting a more efficient and elusive distribution channel is a worrying development.
Also, adopting DGA makes it harder to map Bumblebee's infrastructure, block its domains, and significantly disrupt its operations, adding additional complexity in implementing preventive action against the malware loader.
Source: bleepingcomputer.com
Bạn cũng có thể quan tâm
All Rights Reserved | John&Partners LLC.






