APT36 state hackers infect Android devices using YouTube app clones
The APT36 hacking group, aka 'Transparent Tribe,' has been observed using at least three Android apps that mimic YouTube to infect devices with their signature remote access trojan (RAT), 'CapraRAT.'
Once the malware is installed on a victim's device, it can harvest data, record audio and video, or access sensitive communication information, essentially operating like a spyware tool.
APT36 is a Pakistan-aligned threat actor known for using malicious or laced Android apps to attack Indian defense and government entities, those dealing with Kashmir region affairs, and human rights activists in Pakistan.
This latest campaign was spotted by SentinelLabs, which warns people and organizations linked to military or diplomacy in India and Pakistan to be very wary of YouTube Android apps hosted on third-party sites.
Impersonating YouTube
The malicious APKs are distributed outside Google Play, Android's official app store, so the victims are most likely socially engineered to download and install them.
The APKs were uploaded to VirusTotal in April, July, and August 2023, with two of them being called 'YouTube' and one 'Piya Sharma' associated with the channel of a persona likely used in romance-based tactics.
During installation, the malware apps request numerous risky permissions, some of which the victim might treat without suspicion for a media streaming app like YouTube.
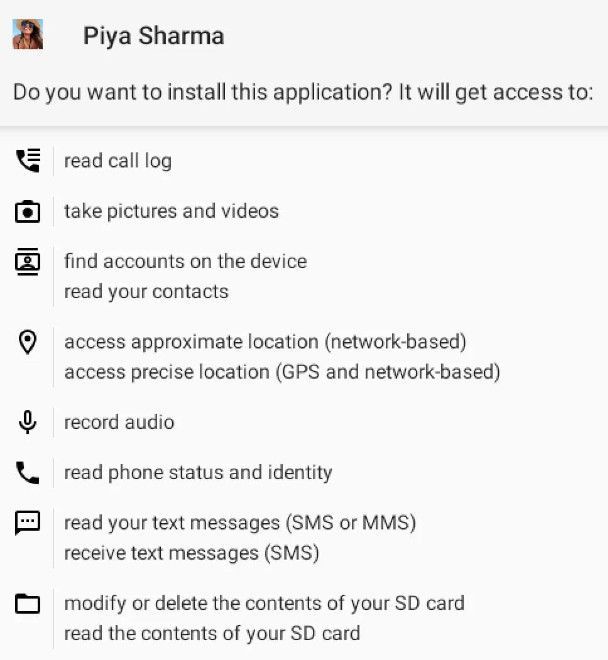
Permissions requested during installation (SentinelLabs)
The interface of the malicious apps attempts to imitate Google's real YouTube app, but it resembles a web browser rather than the native app due to using WebView from within the trojanized app to load the service. Also, it misses several of the features available on the actual platform.
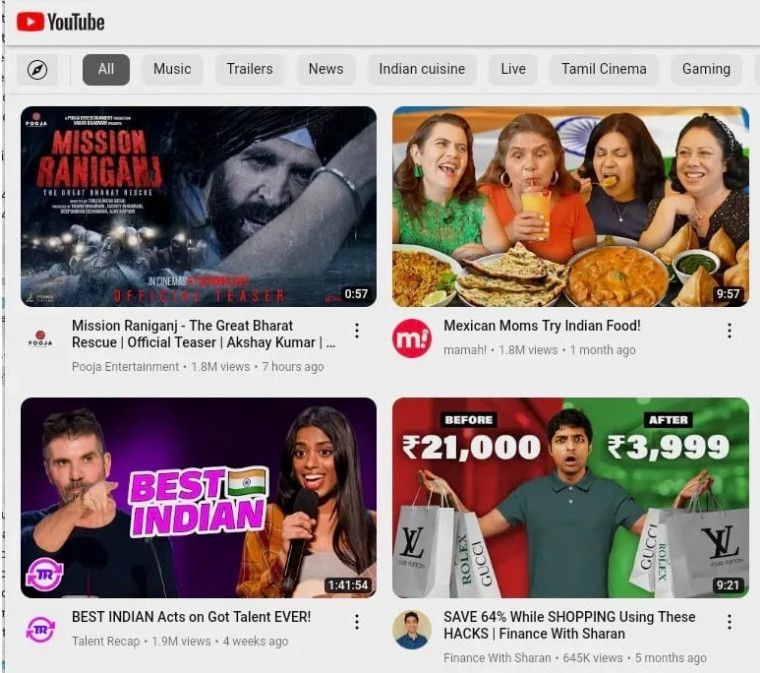
Interface of fake app (SentinelLabs)
Once the CapraRAT is up and running on the device, it performs the following actions:
- Recording with the microphone, front & rear cameras
- Collecting SMS and multimedia message contents, call logs
- Sending SMS messages, blocking incoming SMS
- Initiating phone calls
- Taking screen captures
- Overriding system settings such as GPS & Network
- Modifying files on the phone's filesystem
SentinelLabs reports that the CapraRAT variants spotted in the recent campaign feature enhancements over previously analyzed samples, indicating continuous development.
Regarding the attribution, the C2 (command and control) server addresses CapraRAT communicates with are hardcoded in the app's configuration file and have been associated with past Transparent Tribe activities.
Some IP addresses retrieved by SentinelLabs are linked with other RAT campaigns, though the exact relationship between the threat actors and those remains unclear.
In conclusion, Transparent Tribe continues its cyber espionage activities in India and Pakistan, using its signature Android RAT, now disguised as YouTube, demonstrating evolution and adaptability.
SentinelLabs observes that while the threat group's weak operational security makes their campaigns and tools easily identifiable, their continuous rollout of new apps provides them an elusive edge, consistently reaching new potential victims.
Update 9/21 - A Google spokesperson has sent BleepingComputer the following comment:
Based on our current detection, no apps containing this malware are found on Google Play.
Google Play Protect protects users from apps known to contain this malware on Android devices with Google Play Services, even when those apps come from other sources
Source: bleepingcomputer.com
Bạn cũng có thể quan tâm
All Rights Reserved | John&Partners LLC.






