Apple re-releases zero-day patch after fixing browsing issue
Apple fixed and re-released emergency security updates addressing a WebKit zero-day vulnerability exploited in attacks. The initial patches had to be withdrawn on July 10th due to browsing issues on certain websites.
"Apple is aware of an issue where recent Rapid Security Responses might prevent some websites from displaying properly," Apple said on July 11th.
The company added it would soon release fixed versions of the buggy updates and advised customers to remove them if they were experiencing issues while browsing the web after updating.
While Apple did not share why some websites were prevented from rendering correctly after installing the iOS 16.5.1 (a), iPadOS 16.5.1 (a), and macOS 13.4.1 (a) updates, this likely happened because the new Safari user agent containing an "(a)" string prevented websites from detecting it as a valid version of Safari, causing it to display "browser not supported" error messages.
On July 12th, Apple started pushing iOS 16.5.1 (c), iPadOS 16.5.1 (c), and macOS 13.4.1 (c) Security Response updates that address the web browsing issues.
Apple uses RSR patches to address security issues impacting iPhone, iPad, and Mac devices and to quickly patch vulnerabilities actively exploited in attacks between major OS releases.
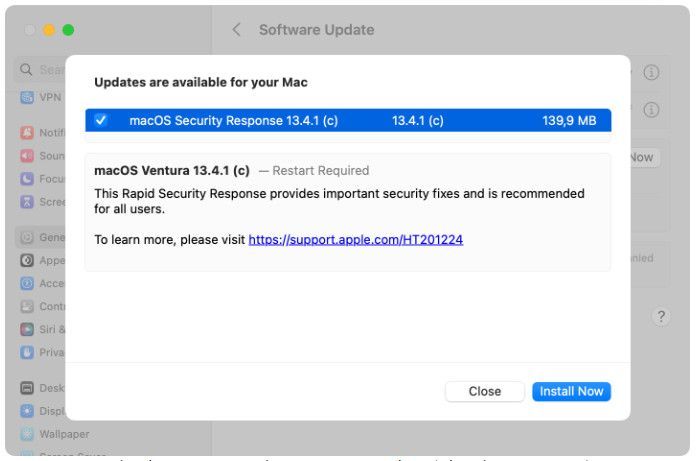
Fixed macOS Security Response update (BleepingComputer)
The zero-day flaw (CVE-2023-37450) patched on July 12th impacts the WebKit browser engine, and it allows attackers to gain arbitrary code execution by tricking targets into opening maliciously crafted web pages.
"This Rapid Security Response provides important security fixes and is recommended for all users," Apple warns customers on devices where these emergency patches are delivered.
"Apple is aware of a report that this issue may have been actively exploited," the company says in iOS and macOS security advisories describing the CVE-2023-37450 flaw patched in today's re-released emergency security updates.
Since the start of 2023, the company addressed a total of ten zero-day flaws exploited in the wild to hack iPhones, Macs, or iPads:
- three zero-days (CVE-2023-32434, CVE-2023-32435, and CVE-2023-32439) in June
- three more zero-days (CVE-2023-32409, CVE-2023-28204, and CVE-2023-32373) in May
- two zero-days (CVE-2023-28206 and CVE-2023-28205) in April
- and another WebKit zero-day (CVE-2023-23529) in February
Source: bleepingcomputer.com
Bạn cũng có thể quan tâm
All Rights Reserved | John&Partners LLC.






